
Competing Interests: The authors have declared that no competing interests exist.
- Altmetric
Current cloud computing causes serious restrictions to safeguarding users’ data privacy. Since users’ sensitive data is submitted in unencrypted forms to remote machines possessed and operated by untrusted service providers, users’ sensitive data may be leaked by service providers. Program obfuscation shows the unique advantages that it can provide for cloud computing. In this paper, we construct an encrypted threshold signature functionality, which can outsource the threshold signing rights of users to cloud server securely by applying obfuscation, while revealing no more sensitive information. The obfuscator is proven to satisfy the average case virtual black box property and existentially unforgeable under the decisional linear (DLIN) assumption and computational Diffie-Hellman (CDH) assumption in the standard model. Moreover, we implement our scheme using the Java pairing-based cryptography library on a laptop.
Introduction
Cloud computing provides various data storage and services over a network [1]. Due to its many benefits, it collaborates with other promising technologies such as 5G networks [2, 3] and IoT [4, 5]. Meanwhile, more individual and corporate gradually outsource data storage or computation to the cloud for its cost saving and convenience. Despite various merits of cloud computing, however in practice, cloud servers are not entirely reliable [6–8]. Since if users directly delivery their data to cloud platforms, the important information in data will be leaked to cloud servers, which will lead to the exposure of users’ privacy. Therefore, the concern is how to secure the data and rely on the services in cloud.
Obfuscation and cryptography are powerful tools that protect the data of users from a malicious/curious cloud server while preserving the services [9, 10]. When user chooses the cloud service to finish computation task without knowing the sensitive information of the task. In this case, the user data are obfuscated before they are forwarded to the cloud server. In a word, the cloud server can finish the computation tasks without sacrificing data privacy [11]. The related researches have addressed various security and privacy issues on data outsourcing. The works in [12–14] proposed cloud storage system in which data were obfuscated and encrypted. Sugumar et al. [15] proposed a confidentiality system named as SUG-DO (SUGUMARDigits Obfuscation) to enhance the security of data in cloud environment. Jin et al. [6] proposed an attribute-based data sharing scheme especially for resource-constrained mobile users in cloud computing. Recently, some new privacy preserving schemes [16–18]for other features have been reported to meet different auditing requirements in the literature.
Threshold cryptography is an essential distributed computational paradigm for enhancing the applicability and the security of public key schemes [19]. This approach was based on the work of Shamir [20], who proposed the definition of (t, n) threshold secret sharing scheme. Using Shamir’s idea, (t, n)-threshold signature [21] separates private keys into n shares distributed to different users, t threshold or more share holders need cooperatively produce a signature. Most existing threshold algorithms rely on the trusted dealers (TDs) to distribute secrets, and more than that, it needs to be always trusted and safeguarded because it has the private key for all users, but they usually do not keep the confidentiality of the data against the cloud. To eliminate the third party, Pedersen [22] was the first to present threshold secret sharing scheme without any TDs. And then, based on the ideas similar to the protocol of Pedersen, Gennaro et al. [23] presented a secure distributed key generation for discrete log based cryptosystems (GJKR’s DKG protocol) that enjoyed a full proof of security. Due to its distributed nature and the lack of a central authority, threshold cryptography becomes one of the most important tools in offering secure applications such as password protection [24] and cloud computing [25]. These studies make great contributions for protecting security of information systems and against various attacks. However, for nontrustable cloud, secret cryptographic keys are potentially vulnerable to attackers, the problem is related to ensuring proper protection of the outsourced computation task.
Program obfuscation is a very hot research topic in the field of practical application points of view, since program obfuscators perfectly conceal important information encoded into programs. A major breakthrough arrived with the work of Barak et al. [26] put forward the concept of program obfuscation into the area of cryptography, their work showed that the construction of generic obfuscation was impossible under the virtual black-box property. Many other impossibility results have been demonstrated in many situations [27, 28]. However, there are a few positive results for some functions in [29, 30]. Faced with the applications of cryptographic functionality, the first ever obfuscated re-encryption was mentioned in TCC’2007 by Hohenberger [31], a new security concept of average case virtual black-box property (ACVBP) was proposed. Succeeding their groundwork, Hada [32] proposed an obfuscator for encrypted signature scheme, and extended the definition of ACVBP, the algorithm was secure under the decisional linear assumption in the standard model. Consequently, several different functionalities and the corresponding obfuscators have been proposed. The research [33] showed a type of obfuscator for verifiably encrypted signatures. The obfuscation of encrypted group signature (EGS) was studied in [34], where the notion of ACVBP w.r.t R(C) and T(C) was defined. To provide secure authentication, Yang et al. [35], applied an obfuscator to anonymous authentication, the algorithm supported batch verification of authentication requests, realizing the improvement of efficiency. In order to make obfuscation application into cloud computing, Zhang et al. [36] proposed an obfuscator for all polynomial-size CNF circuits and used to cloud computing. Zhang et al. [37] proposed an obfuscator for encrypted verifiable encrypted signature, and modelled the application in electronic transactions. The obfuscation can achieve a series of applications, threshold signature is an attractive service used in cloud computing, this paper focuses on achieving encrypted threshold signature, which designs an obfuscator to protect users’ privacy. It should offer outsourcing computation without compromising data privacy.
However, the existing threshold cryptography mainly focuses on how to afford secure data for users, few works consider another requirement for the cloud application that needs to protect the sensitive data. In order to protect the privacy of the information sent from the user to the cloud, our work follows the idea of Hada’s work and applies it to threshold signature setting. In this paper, we propose a secure obfuscation for encrypted threshold signature. The main contributions are as follows:
We propose an obfuscator that implements encrypted threshold signature (ETS) functionality, which can outsource the threshold signing rights of users to cloud server securely by obfuscation. Besides, this method can protect the sensitive leakage from the ETS program running on an untrusted sever.
We propose some security notions of ETS functionality and the corresponding obfuscator. Under the decisional linear assumption and computational Diffie–Hellman assumption, the proposed obfuscator satisfies the requirements of ACVBP and existentially unforgeability in the standard model.
We analyze the correctness of functionality preservation and polynomial slowdown. Meanwhile, the performance analysis of ETS functionality and the obfuscator are provided. Finally, we implement the proposed algorithms in a personal computer by using java pairing-based cryptography library.
The remainder of this paper is organized as follows. In section 2, we present some preliminaries including bilinear pairings, security problems and circuit obfuscators. In section 3, we present some build blocks will be used in our proposed schemes, then we propose an encrypted threshold signature scheme and the corresponding obfuscator based on linear encryption scheme and threshold signature. Section 4 analyzes the security and performance of our scheme from the perspectives of functionality preservation, ACVBP and existentially unforgeability. Section 5 presents our conclusion.
Preliminary
Bilinear pairings and security problems
In this section, we describe bilinear maps and hard problems [38]. Let consider two cyclic groups and
Bilinearity: For all
Non-degeneracy: There exists
Computability: For all
Definition 1. The Decision Linear (DLLN) Problem is to decide whether a + b = c, given
Definition 2. The Computational Diffie-Hellman (CDH) Problem is that, given
Circuit obfuscators
In this section, we briefly review some notations of circuit obfuscators used in this paper [32]. We use
Definition 3. [32] The statistical difference between C0(x) and C1(x) is given by:
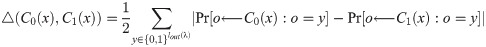
Definition 4. (Preserving Functionality) [32] A PPT machine Obf is a circuit obfuscator for a class of probabilistic circuits
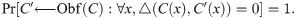
Obfuscation of encrypted threshold signatures
Encrypted threshold signatures (ETS) functionality utilizes a threshold signature (TS) scheme, which was proposed in [21] and an asymmetric linear encryption scheme [39]. After that, we will give a detailed description of obfuscation.
TS signature
The TS signature scheme is a tuple of algorithms ∏ = (Setup, Share-Sign, Share-Verify, Combine, Verify) such that:
Setup(params, λ, k, n): Takes as input a security parameter Choose system parameter To generate public key, n users jointly generate user public key g1 = gα by using GJKR’s DKG. Each user Pi broadcasts gf(i) for a random jointly generated degree k − 1 polynomial User Pi gets the private key shares SK = (sk1, sk2, ⋯, skn) as Output the public key p = (VK, params, g1, g2, u′, U), and each user is supplied with the private key share ski.
Share-Sign(ski, m): To sign m = m1
m2 ⋯ mn ∈ {0, 1}n, using ski, choose
Share-Verify(p, m, i, σi): Given a signature share σi, and the verification key vki, the partial verification algorithm return 1 if
Combine(p, m, i, σi)i∈Φ: For each i ∈ Φ, where a subset Φ ⊂ {1, 2, ⋯, n} and |Φ| = k. Let λi be the Lagrange coefficients so that
Verify
Linear encryption scheme
The linear encryption scheme consists of three algorithms ∑ = (Key generation algorithm(KG), Encrypt algorithm(Enc), Decrypt algorithm(Dec)), the algorithms are described as follows:
KG(params): Parse system parameter
Enc(m, pke): To encrypt message m, randomly choose 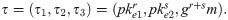
Dec(τ, ske): Given τ and ske, compute
Specifically, we denote the rerandomization algorithm by ReRand(p, pke, (τ1, τ2, τ3)), which produces a new ciphertext
The ETS functionality
ETS functionality is composed of ETS.Setup, ETS.Sign, ETS.Verify. We give the concrete construction as follows:
ETS.Setup(params, λ, k, n):
Parse parameter For users(participants), generate public keys and private shares by running (VK, params, g1, g2, u′, U, SK)← Setup(params, λ, k, n). For receiver(verifier), randomly choose
ETS.Sign(SK, m, p, pke): For m = m1
m2⋯mn ∈ {0, 1}n, works as follows:
Randomly choose Verify the validity of signature σj by
Compute the combined signature Randomly choose Output encrypted threshold siganture (S1, S2).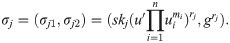
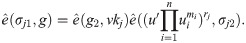
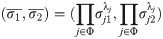
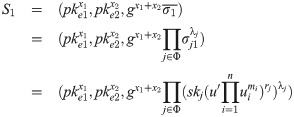
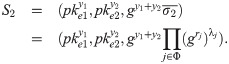
ETS.Verify(p, ske, S1, S2, m): Parse p = (VK, params, g1, g2, u′, U), and m = m1
m2⋯mn ∈ {0, 1}n. Decrypt (S1, S2) to get 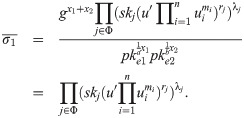
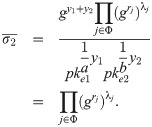
The obfuscation of ETS functionality
From the description of the ETS functionality in above section, we regard a family of circuits
Obf
Extract system parameters (pke, SK, p). Parse parameter For each j ∈ {1, 2, ⋯, n}, randomly choose Construct an obfuscated circles Rp,pke,t that contains the values
Rp,pke,t: The obfuscated circuit can be executed on any untrusted cloud server, and it does the following.
On input security parameter λ, the circuit outputs (pke, p). On input message m = m1
m2⋯mn ∈ {0, 1}n, randomly choose Verify the validity of signature Compute the combined signature Compute Randomly choose Output 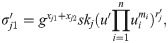
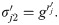
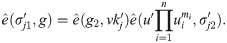
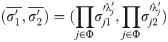
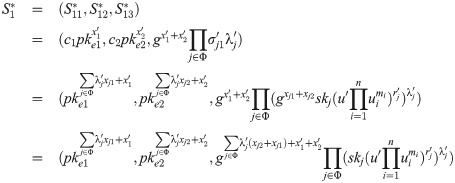
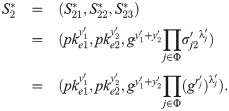
Besides, the polynomial time property is evident as all the calculation here is valid in polynomial time. It is easily to verify that the obfuscated program by theorem 1.
Theorem 1. The algorithm Rp,pke,t can pass verification.
Proof 1. For a valid ciphertext
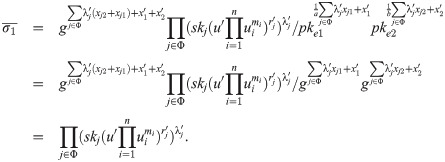
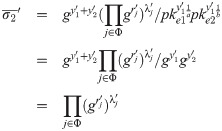
The following equation shows that Rp,pke,t satisfies correctness:
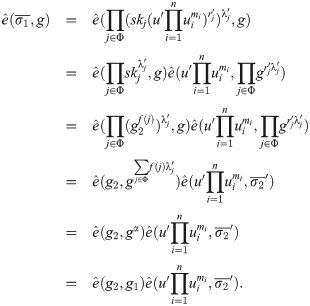
Security properties
In the threshold cryptosystem, we should consider a coalition of k curious but honest users attack against the proposed obfuscator. Therefore, we suppose that an adversary is capable of obtaining the private key shares of corrupted users against the obfuscator, excepting the user who generates the obfuscated implementation as a challenge, that is, an adversary can access the corruption oracle on any corrupted user, but corrupt up to k − 1 of the n players, the set of oracle restrictions dependent on C is defined as R(C). In this paper, we define R(C) = {Corruption, ∣Φ∣ ≤ k − 1}, which can be expressed as Corruption∣Φ∣≤k−1. Some security requirements of the proposed obfuscator are introduced in the following descriptions.
Definition 5. [34] An obfuscator Obf for C meets the ACVBP w.r.t. dependent oracle set T(C) and restricted dependent oracle set R(C) if the following situation holds: There exists a PPT simulator S such that, for distinguisher D, arbitrary polynomial f, all sufficiently large
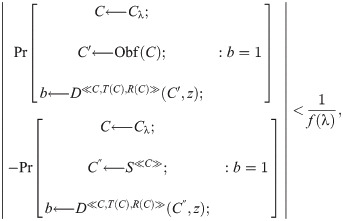
Definition 6. Let (KG, Enc, Dec) and (Setup, Share − Sign, Share − Verify, Combine, Verify) be a couple of linear encryption and the threshold signature algorithms. The threshold algorithm is existentially unforgeable w.r.t. ETS functionality if the following situation has to be satisfied: There exists a PPT algorithm A, all sufficiently large
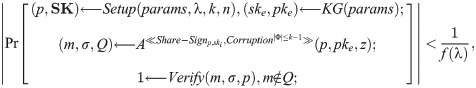
Definition 7. Let (KG, Enc, Dec) and (Setup, Share-Sign, Share-Verify, Combine, Verify) be a couple of linear encryption and the threshold signature algorithms. The threshold signature algorithm is existentially unforgeable w.r.t. the ETS Obfuscator if the following situation has to be satisfied: There exists a PPT algorithm A, all sufficiently large
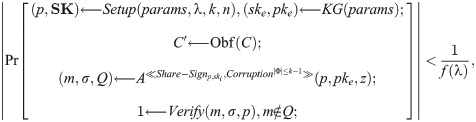
Correctness
In this section, we identify the following goals that the obfuscator for ETS should satisfy.
Correctness: The correctness of an obfuscator requires “Preserving Functionality” as described in Definition 4.
Security: The obfuscator needs satisfy ACVBP with respect to T(C) and R(C) and existentially unforgeable with respect to ETS Obfuscator.
Below, we state the Theorem 2 which is a key result used to show the correctness of our construction.
Theorem 2. (Preserving Functionality) The obfuscated program preserves the functionality of original ETS.
Proof 2. On receiving the encrypted threshold signature (S1, S2), that is
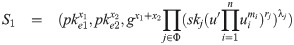
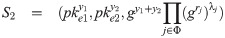
On receiving the obfuscated program
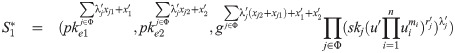
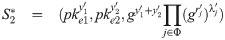
We observe that both (S1, S2) and
Security proof
Theorem 3. Under the DLLN assumption, the algorithm ObfETS
is ACVBP with respect to dependent oracle
Proof 3. Suppose
The detailed procedure of S is as below.
Using the sampling access to
Parse p = (V
K, params, g1, g2, u′, U), V
K = (vk1, vk2, ⋯, vkn) and
Randomly choose
Encrypt Junki
using public key pke,
Compute
Set Junk = (ci1, ci2, ci3), where i = 1, 2, ⋯, n.
Output
We will first prove that the output distributions of the simulator and the obfuscator are indistinguishable. We prove this by contradiction, assume that the probability that a distinguisher D≪C,T(C),D(C)≫ can distinguish between the probabilities described is not negligible. That is, |PrNick − PrJunk| is not negligible.


Assume that the probability of D to win is not negligible, then we build a couple of adversaries (A, B), which attacks the semantic security of the encryption algorithm. First, A does as below:
Take as input (params, pke, p, z).
Parse
Generate the signers’ private key shares S K.
Parse S K = (sk1, sk2, ⋯, skn).
Randomly choose
Set m1 = ski and m2 = Junki.
Output (m1, m2, pke).
Given an encryption ciphertext ct of mi, the algorithm B can make a distinction between m1 and m2 by utilizing D.
Take as input (p, pke, m1, m2, ct, z).
Parse
Simulate
Output D’s output.
The advantage of attacker B is the same as the advantage of the distinguisher D to distinguish the output distributions of obfuscator and simulator. So if it’s not negligible, then it contradicts the DLLN assumption. Thus the advantage of D is negligible when given one tuple of ciphertexts, then the advantage when given three tuples is also negligible. So we conclude that the obfuscator satisfies ACVBP with dependent oracle set T(C) and restricted oracle setR(C).
Theorem 4. If ObfETS
for ETS functionality is ACVBP w.r.t. dependent oracle
Proof 4. The proof of this theorem is very similar to the proof in [32], see [103, Theorem 1], we thus omit the formal proof here.
From Theorem 3 and Theorem 4, the TS scheme satisfies the existentially unforgeable, even if the adversary can obtain the obfuscated circuit. The obfuscator for ETS is mainly to enhance the security, and it is safe for the obfuscation circuit to be executed by any untrusted cloud server, and the cloud server could not get any useful information from it.
Corollary 1. Under DLLN and CDH assumptions, TS scheme is existentially unforgeable w.r.t. ObfETS.
Experimental results
Theoretical performance analysis
Here we analyze the performance efficiency of our scheme, in terms of computational complexity when performing ETS.Sign, ObfETS, Rp,pke,t and ETS.Verify operations. The result is showed in Table 1. In this table, Rand denotes the operation that randomly selects element, Add denotes addition, Mult denotes multiplication, Exp be an exponent operation, Inv denotes inverse operation. As shown in Table 1, the computational complexity of ETS.Sign and Rp,pke,t algorithms is linear in the number of n and k. All these operations are polynomial bounded operations and can be computed effectively. Therefore, all algorithms are efficient from a theoretical perspective.

| Operation | ETS.Sign | ObfETS | Rp,pke,t | ETS.Verify | |
|---|---|---|---|---|---|
 | Rand | n + 4 | 2n | n + 4 | 0 |
| Add | 2 | n | 2k | 0 | |
| Inv | 0 | 0 | 0 | 4 | |
 | Mult | 2k + n + 1 | 2n | 4k + n + 1 | 0 |
| Exp | 2k + 2n + 6 | 3n | 4k + 2n + 6 | 4 | |
| Inv | 0 | 0 | 0 | 2 | |
 | Mult | 1 | 0 | 1 | 1 |
 | Pair | 3 | 0 | 3 | 3 |
Implementation
To provide numerical results, we implement it to measure the performance of our scheme. Our implementation is written in C using the Pairing-Based Cryptography Library [40]. For the computations, we use the curve groups that are implemented in the Libpbc library. The computations are run on a PC with 3.70 GHz CPU frequency, and 4 GB of RAM. In the experiment, we use elliptical curves with a base field size of 512 bits and an embedding degree of 2. The security levels are selects as |p| = 512.
The following results denote the average running times of related cryptographic operations. In the experiment, the experimental result is the average number of 10 runs. We measure the running time of four algoritms, that is: ETS.Sign, ObfETS, Rp,pke,t and ETS.Verify. The performing consequence of our scheme is provided in Fig 1 when n = 5 and k = 3. It is shown that the obfuscated implementation have high efficiency in general, because the algorithm needs perform more exponent operation.

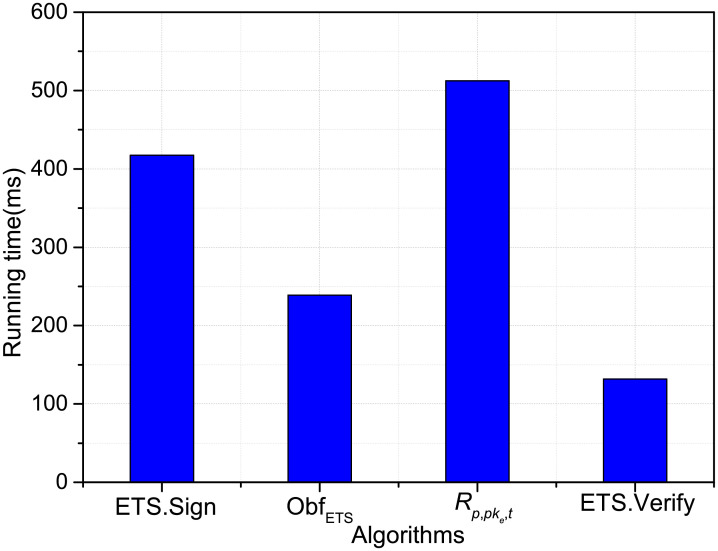
Execution time of the algorithms.
Figs 2 and 3 show the time variety when the number of n and k as variables, respectively. Fig 2 shows the operations time of ETS.Sign, ObfETS and Rp,pke,t when k is set as 3 and the number of n is set varies from 5 to 9 increased by an interval of 1. Fig 3 shows the execution time of the three algorithms when n is set as 7 and the number of k is set varies from 3 to 7 increased by an interval of 1. We observe that Rp,pke,t, ETS.Sign and ObfETS’s time cost increases fastly along with the increasing of n and k. It can be seen from the results that Rp,pke,t is more costly than ETS.Sign with the same n or k.

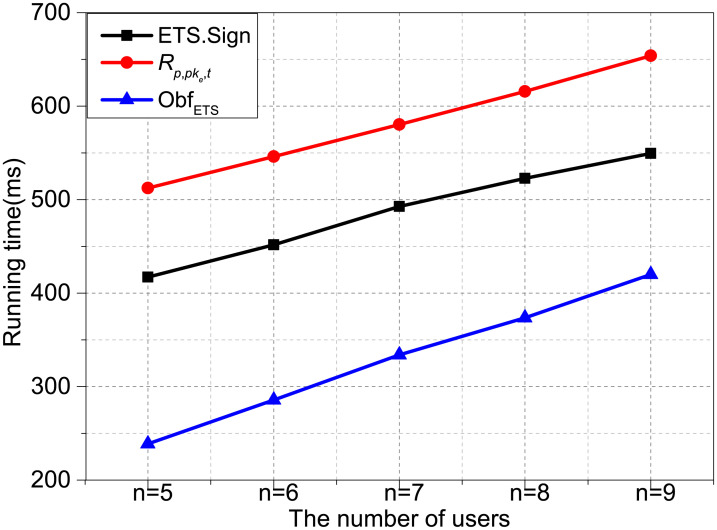
Time cost with k = 3.

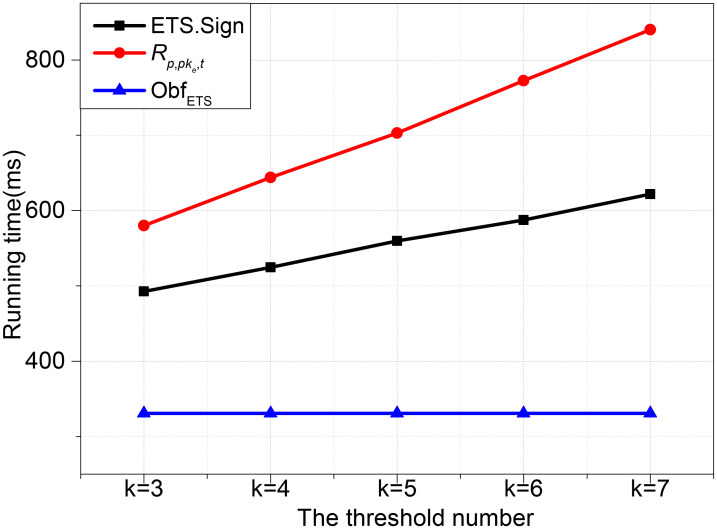
Time cost with n = 7.
Conclusion
Obfuscation technique can provide much greater security for sensitive data from service providers in cloud computing. In this paper, we design an obfuscator for encrypted threshold signature, according to this technique, key shares are obfuscated before they are uploaded to the cloud services. In this regard, we can implement the program obfuscator run on a untrusted cloud sever, while hiding privacy-related sensitive information from the obfuscated program. The security analysis demonstrate that our scheme can meet the average case virtual black box property.
Acknowledgements
The authors would like to thank the anonymous reviewers of this paper for his/her objective comments and helpful suggestions while at the same time helping us to improve the English spelling and grammar throughout the manuscript.
References
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
 Obfuscating encrypted threshold signature algorithm and its applications in cloud computing
Obfuscating encrypted threshold signature algorithm and its applications in cloud computing
