
- Altmetric
Percolation is an emblematic model to assess the robustness of interconnected systems when some of their components are corrupted. It is usually investigated in simple scenarios, such as the removal of the system’s units in random order, or sequentially ordered by specific topological descriptors. However, in the vast majority of empirical applications, it is required to dismantle the network following more sophisticated protocols, for instance, by combining topological properties and non-topological node metadata. We propose a novel mathematical framework to fill this gap: networks are enriched with features and their nodes are removed according to the importance in the feature space. We consider features of different nature, from ones related to the network construction to ones related to dynamical processes such as epidemic spreading. Our framework not only provides a natural generalization of percolation but, more importantly, offers an accurate way to test the robustness of networks in realistic scenarios.
Network robustness is usually assessed following topological criteria, but disregards the role played by non-topological information. Artime et al. propose a flexible percolation framework that overcomes this limitation and combines both dimensions, offering new ways to protect real systems.
Introduction
Classical percolation is a toy model in which one deletes nodes from a low-dimensional regular lattice and computes different properties, statistical and geometrical, of the remaining isolated clusters. Although firstly considered as a gelation problem in the context of macromolecules1, it is not until the development of the theory of critical phenomena2 that percolation drew a great deal of attention to the physics community. The reasons were, at least, twofold. On one hand, percolation provided stimulating theoretical challenges, considered one of the simplest models displaying a phase transition, without any need of introducing dynamics or thermodynamics quantities, as it occurs in the Ising model3, for instance. On the other hand, percolation was flexible enough in its definition to be mapped to many diverse problems, such as the dielectric response of inhomogeneous materials4, epidemiology5 or flows in porous media6, among many other7,8.
The interest in percolation is renewed with the advent of modern network theory9. A network, broadly construed, is a set of nodes with arbitrary connections among them, contrary to lattices, that are regular structures embedded in spaces of finite dimension, with all of their nodes having the same number of edges, i.e., same degree. In this context, the fraction of removed nodes are usually thought of as failures or attacks, and the largest connected component after the perturbation has a functional interpretation assumed to be the part of the network that is still operative. Therefore, percolation in this type of topologies has brought a deeper understanding of the robustness and resilience of real-world networked systems10–13, as well as, from a fundamental perspective, it has provided new analytical techniques14,15 and interesting phenomenology from the standpoint of statistical physics16–19.
Since in networks the degree of nodes is distributed heterogeneously, one can exploit this fact to devise new physically meaningful removal strategies, such as targeting nodes from higher to lower degree14,20. These interventions on the networks are called attacks since they are intentionally performed using some a priori information. Studying percolation based on degree attacks elucidates the role played by large degree nodes, the hubs, on the network robustness. For instance, graphs with long-tailed degree distributions are very weak to hub removal, that is, by removing a very small number of hubs the network is broken into many small components. This has catastrophic consequences for the security of real-world networks since many of them display such degree distributions21.
The degree is the most basic centrality measure in complex networks. However, there exist a plethora of alternatives to assess the importance of a node within a graph22–24, and accordingly, we can test the importance of these variables on the network robustness by performing attacks based on them25–27 and evaluate how far is each attack strategy from being optimal28. Moreover, nodes could be characterized by non-topological properties as well, such as age29, biomass30, or bank credibility31. Hence, similar network attacks can be implemented to test percolation properties of the system when a group of nodes with certain characteristics is removed, for instance, those users of online social platforms generating or spreading hateful content10.
Taking into account that in many relevant situations singular information is accessible at a node level, it is desirable to have a method to quantify the impact of intervening in the network following alternative protocols based on these non-topological features. We tackle therefore the challenge of developing a percolation framework that accounts for both topological and non-topological information simultaneously. The latter element will be considered as node metadata, what we call the features. We generalize standard message-passing methods by introducing a joint degree-feature probability density function on the network. Several percolation quantities, such as the critical point or the size of the giant component are computed. We check the validity of our theory by confronting the analytical estimates with synthetic and real-world networks, finding an excellent agreement.
The rest of the paper is organized as follows. We first motivate the usefulness of feature-enriched percolation by presenting some examples of real-world networks with different degree-feature correlations and proposing virtual dismantling experiments on them. Next, the model is presented and we work out the analytical expression for the size of the giant component in terms of a generic degree-feature joint probability function. We then confirm the analytical predictions in synthetic networks, discussing separately the cases of uncorrelated and correlated degree-feature distributions. We also test the validity of our theory in random geometric graphs (RGGs), which are known to be highly spatially correlated, and therefore, message passing methods may fail to accurately predict the percolation point. A final section is devoted to the very interesting case in which the features are related to variables coming from dynamic processes running on top of networks. We investigate these latter cases in both synthetic and real-world networks. We close the article by drawing conclusions.
Results
Empirical evidence of non-trivial feature distributions
In this section, we report different patterns of feature distributions in real-world complex networks. The chosen examples are arbitrarily selected based on our biases, but they are not, by no means, an exception. Indeed, when collecting real data to construct network structures, most of the times the nodes have some associated properties, or metadata, that individually characterize them beyond their degree.
The first example corresponds to a board interlock network, i.e., a bipartite system of directors and companies. Links between them exist whenever a director holds a seat on the corporate board of a company, and nothing prevents a director to sit on more than one boardroom. We regard the feature as the age of the members of the board. We see that, in this case, the average age of the directors is uncorrelated with respect to their degree, see Fig. 1a. Nevertheless, the spread of the distribution as a function of the degree is not constant. Hence, feature-enriched percolation in this example can help reveal the role played by directors of a certain age on the global connectivity structure of the system.

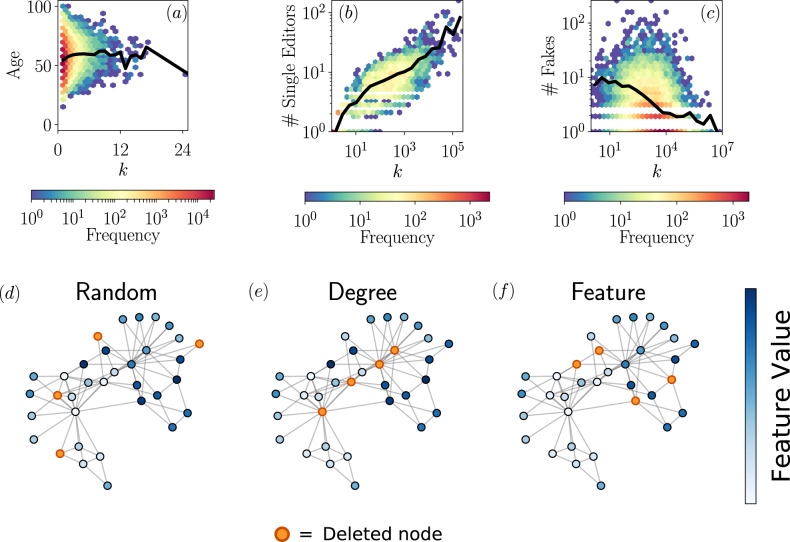
Empirical evidence of different feature-degree patterns and sketch of different types of removal protocols in the percolation process.
a Correlation between the degree of a director of a company (number of companies in which she participates) and her age. Data from67. b Wikipedia pages show a positive correlation between the hyperlinks present in an article (out-degree) and the number of unique editors that have modified such article. Data from an updated version of the ref. 68. c Negative correlation between the number of followers and the number of fake news posted by a user. The subset of data taken from69, comprising worldwide users during the first two weeks of April 2020. The black solid lines correspond to the mean value of the data. In the bottom row, we show how different interventions can affect the network. In the random case (d) nodes are chosen equiprobably to be deleted. In the degree case (e), the removed nodes are those with the largest number of connections. In the feature case (f), the selected elements are those with the largest value of the feature (the darkest blue). In this example, the values of the feature have been assigned manually for convenience and the feature vector F has been considered unidimensional.
The second example belongs to the context of crowdsourced creation of cultural content. We take the snapshot of the current version of Wikipedia, in which nodes are articles and edges are the hyperlinks among them. Moreover, for each node we keep track of the number of revisions that it has suffered since its creation, and how many unique users have participated in these edits. We see that the correlation between the degree of a Wikipedia page and its number of unique editors is positive and heterogeneously distributed, see Fig. 1b. With the framework of feature-enriched percolation, we are able to remove nodes with a certain degree-feature pattern, thus, for example, one can be interested to assess how the navigability across this knowledge corpus is modified under the removal of well-connected articles that do not show enough levels of collaborative edition, i.e., that have been written by too few users.
As a final example, we present a system that displays a negative correlation among degree and feature, see Fig. 1c. It corresponds to misinformation propagation in the online social platform Twitter. We take a sample of messages within a two-week time window during the COVID-19 pandemic and consider only messages that share an url in the text. The nodes are users, where the degree is their number of followers, and the feature is the number of fake news that they have posted. We see that the average number of fake news tends to decrease as the visibility of Twitter accounts is higher, varying broadly in this case as well. Feature-enriched percolation can be helpful, for example, to shed light on the problem of how to guarantee the information spreading while cutting off users that systematically share dysfunctional and harmful content.
The model
Let us take the ensemble of networks generated via the configurational model9, with a degree sequence obtained from a degree distribution pk. We assume that each node is characterized by its degree k and by a set of features F = (F1, F2, …, FM), with . The degree distribution is considered discrete and the feature distribution can be considered either discrete pF or continuous p(F). Throughout the article, we shall assume that features are continuous, but reproducing the results for a discrete domain is straightforward. The joint probability is indicated by P(k, F). We define the occupation probability ϕk,F as the probability that a node with degree k and feature values F within the interval [F, F + dF] have not been removed from the original network. Our goal is to find the position of the critical point and the size of the giant connected component S as a function of the parameters of P(k, F) and ϕk,F32.
Let u be the average probability that a node with k connections and feature values F does not belong to the giant component via one of its neighbors. The probability that it does not belong to the giant component is uk. Thus, the probability that the node belongs to the giant component due to a neighbor state is 1 − uk and has to be multiplied by ϕk,F, which determines whether or not the node itself is present in the network. Averaging this quantity over degrees and features we obtain ∫dF∑kϕk,FP(k, F)(1 − uk), where ∫dF is an M-dimensional definite integration over the elements of the feature vector. This is identified as the average probability of finding a node in the giant cluster, or equivalently, the fraction of nodes in the giant component. Therefore
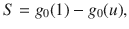
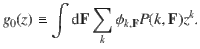
To solve Eq. (1) we need to obtain an expression for u. This can be achieved by writing a self-consistent equation that has two contributions. On the one hand, a neighbor might not be in the giant component because it has been deleted, which occurs with probability 1 − ϕk,F. On the other hand, if the neighbor has not been removed, it should not belong to the giant component via any of its other ke neighbors. ke is called the excess degree distribution, and it is equal to ke = k − 1. This happens with probability
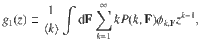
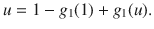
Notice that the relation between generating functions held in ordinary percolation is valid here as well, i.e., g1(z) = ∂zg0(z)/〈k〉. It is important to also note that our generating functions, although including the M-dimensional integral in the definition, depend only on one variable since the feature enrichment does not add any new information in terms of connectivity. Therefore, our framework should not be taken equivalent, for instance, to the study of percolation in graphs with colored edges33, in general multilayers34, in networks with multi-type nodes35 or in interdependent systems36, where multivariable generating functions are common.
The occupation probability ϕk,F allows us to understand the role played by certain values of degree and/or features in the connectivity of the network. The classical percolation, where nodes are removed in a uniformly random fashion, is recovered by selecting a constant function ϕk,F = ϕ ∈ [0, 1]. The case of removing the most connected nodes is recovered by setting ϕk,F = θ( − (k − k0)), being θ(⋅) the Heaviside step function and k0 a threshold such that all nodes with degree larger than it are removed. Similarly, one can apply the same arguments in the feature space, and study the case in which all nodes with a feature larger than a threshold are deleted ϕk,F = θ( − (F − F0)). These three examples are sketched in Fig. 1.
Applications
To illustrate and check the validity of the theory, we investigate several examples. For the sake of simplicity we focus on unidimensional feature vectors, i.e., F = F. First we address the case of independent degree and feature, i.e., P(k, F) = pkP(F). We then move to consider joint distributions which are positively and negatively correlated. These latter cases leave the nature of the feature undetermined. In this section, though, we also address problems in which the features are related to the distance in a geometrical space and to dynamical processes evolving on top of the network.
Independent case
Let us consider a network with degree distribution and feature distribution
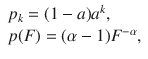
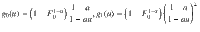
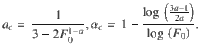

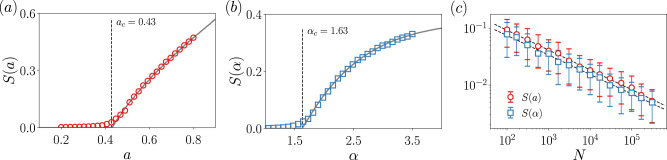
Size of the giant component for the independent degree-feature case.
Solid lines are computed from the theory, the markers come from simulations. In (a), the control parameter a is related to the topology, while in (b) the control parameter α is related to the feature distribution, see Eq. (6). Vertical lines indicate the value of the critical point computed from the theory, see Eq. (8). System size is N = 3000 and each point is computed by averaging over 100 independent realizations. In (c), the size of the giant component with error bars as a function of the system size, together with the fits to the data.
We investigate the universality class of the percolation process for independent feature-degree distributions, in order to figure out whether the introduction of features modifies the critical properties of mean-field percolation. Here we understand mean-field as the behavior of classical percolation in regular lattices of dimension d ≥ dc = 6. The critical properties of complex networks, which are infinite-dimensional entities, might not be the same as mean-field, if, for instance, the underlying degree distribution is power-law16 or the removal process is modified37. Note that in feature-enriched percolation we will necessarily have two parameters, one controlling the topology and another the features. Hence, for the size of the giant component, we write
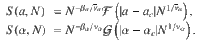
Positively correlated case
Let us consider now the more interesting and realistic case of a joint distribution in which feature and degree are not separable. We take one of the simplest scale-free distributions that are positively correlated,
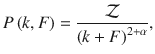
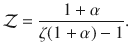
In practical terms, to assign the values of the degree and the feature in the simulations, we first construct the network from the configurational model with a degree sequence drawn from pk = ∫dFP(k, F). Then, depending on the degree of each node, we draw a random variable from the conditioned distribution P(F∣k). Randomized versions of the system are possible either by randomly shuffling the feature of the nodes in the correlated network or by constructing a new network from pk and assign features from P(F).
Considering again the removal of all nodes with feature value above a threshold F0, the generating functions are
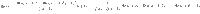
The theoretical predictions are compared with the simulations in Fig. 3a, finding an excellent agreement. Another curve is also displayed, corresponding to the randomized version of the correlated model Eq. (10), and that serves to single out the role of the degree-feature correlations in the behavior of the size of the giant component. It is immediate to observe that the critical point and the size of the giant component are smaller for the correlated case than for the randomized case. This holds true for all feature thresholds, being the separation among both the critical points and the S more accentuated as F0 decreases. The rationale behind this is the following: the marginal feature probability P(F) is the same for both cases, so for a given threshold F0 the same fraction of nodes is removed, although the chances of hitting a low-degree node are much larger in the randomized case than in the correlated case, due to, precisely, the degree-feature correlation. Since targeting hubs it is a very fast way of dismantling a network, it is natural to observe a smaller critical point and a smaller size of the giant component. A quantitative way to measure the deviations caused by degree-feature correlations with respect to the uncorrelated scenario is to compute the area between both curves,
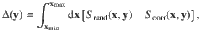

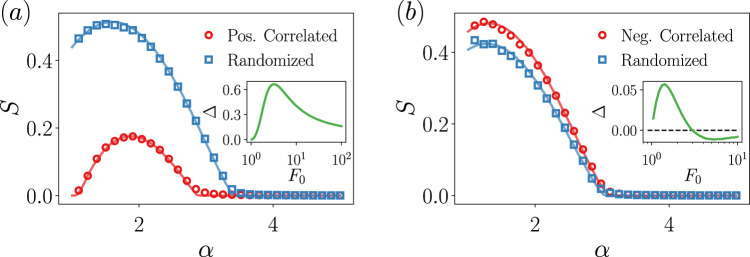
Percolation in correlated degree-feature networks.
Size of the giant connected component for (a) the positively correlated distribution Eq. (10) and for (b) the negatively correlated distribution Eq. (14), and their randomized counterparts. All nodes with feature F ≥ F0 = 3, are removed. Points are the results from simulations and the solid line comes from the theory. Network sizes are N = 216 and each point is averaged over 100 realizations. In the inset of the panels, we display Δ(F0), corresponding to the area between the randomized and correlated curves and defined in Eq. (13), as a function of the feature threshold. The integral has been computed in the region α ∈ (1, 5].
Figure 3a also shows a striking peculiarity: the non-monotonicity of the giant component and its approach to the non-percolating regime S = 0 when α → 1. In Supplementary Note 5, we give an explanation for this behavior and show that there are no critical properties in the vicinity of α = 1. This approach to the non-percolating phase is a genuine effect of the degree-feature correlation that would be missed if the correlation is disregarded. In other words, the robustness of this positively correlated system under the attack to its most prominent nodes in the feature space would be overestimated if correlations are ignored. In Supplementary Note 6 (see Supplementary Movies 1 and 2 as well) we also address the critical properties of this positively correlated network model, where we show that it shares the same critical exponents as the mean-field percolation.
Negatively correlated case
Contrary to the last section, there are certain situations in which peripheral, low degree nodes might be the ones carrying the largest feature values. Again, we model this scenario with an ad hoc negatively correlated joint distribution, one of the simplest displaying power-law behavior39:
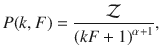
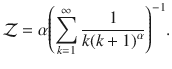
The generating functions corresponding to Eq. (14), and for the same occupation probability as the other examples, are
The comparison between the theoretical predictions and the simulations for the negatively correlated distribution is given in Fig. 3b, both for the correlated distribution and its randomized version, finding again a very good agreement. We observe that in this case the behavior is reversed with respect to what is found in the positively correlated case. The critical point and the size of the giant component for the anticorrelated networks are slightly higher than the one for the randomized counterparts. However, surprisingly this behavior depends on the feature threshold employed. Depending on the F0, we might be in regimes in which disregarding the negative degree-feature correlations leads to an underestimation or to an overestimate of the robustness, see the inset of Fig. 3b. Similarly to the positively correlated case, Δ is non-monotonic and there is an intermediate threshold value for which the underestimation is maximum, but increasing F0 even more we find the point at which the overestimation is maximum. This evinces the non-trivial phenomenology that arises even in these simple cases of ad hoc correlations.
Features related to the network construction
Let us now consider a case where the degree and feature distributions are not imposed exogenously but they emerge naturally from the network construction process. As an example, we consider RGGs, which are especially useful to model situations in which there is some kind of physical contact or proximity between the units of the system, and they find applications in areas as diverse as wireless sensor architectures41, population dynamics42, or consensus formation43, to name but a few. Even though percolation has been widely studied in RGGs in the mathematical literature (see, e.g., Refs. 44,45), critical points are known up to some bounds46, and because of the strong topological correlations of RGGs, tree-like approximations, in general, are not as accurate as in the case of infinite-dimensional networks. On this basis, we will need to quantify the discrepancy between theory and simulations and how it scales with the link density.
We consider RGGs composed of N nodes, placed uniformly at random on [0,1)2 with periodic boundary conditions. Two nodes are connected if they are within a distance r. We take the feature as the distance between a node and its closest neighbor dmin, i.e., F ≡ dmin, and we delete those nodes that have the nearest neighbor at a distance smaller than a certain threshold r0 > 0, i.e., ϕF = θ(F − r0) (see Fig. 4a). This scenario can be relevant, for instance, in spatial ecological models in which there is a competition for resources47,48. Note that this particular choice of the occupation probability is made for illustrative purposes, and without much effort, one could envision other relevant scenarios, for example, with ϕF = θ( − (F − r0)) or that take the distance to the furthest neighbor dmax as the feature. In all these mentioned cases, the generating functions can be calculated.
To compute the generating functions we first need the joint probability function. Its calculation is detailed in Supplementary Note 7. Setting a maximum bound kmax = N − 1 in the degree distributions, the generating functions are
The analytical calculations are compared with simulations in Fig. 4b. We keep the radius of interaction r constant and discuss the results as a function of the number of nodes in the network. First of all, we see that the position of the percolation point is inversely proportional to N. This behavior is somehow expected: the larger the system size, the denser the network, so the probability of nodes to have neighbors at distance smaller than r0 becomes high, hence the rapid network dismantling. Moreover, we see that when the system size is low, the theoretical results systematically overestimate the value of the giant component. Note that this is not a finite-size effect as it occurs in other systems displaying phase transitions, but inherent limitations of the theory due to the topological correlations present in RGGs and not captured in their degree-feature distribution. We can quantify this discrepancy following the rationale of Eq. (13) but taking the absolute value in the integrand. Thus,
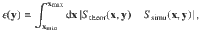

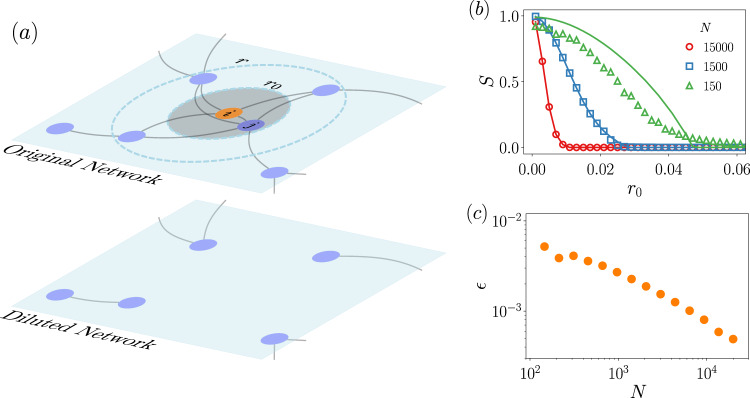
Feature-based percolation in random geometric graphs.
In (a), a sketch showing how the removal of nodes proposed in the main text works: if a node i (central orange marker in this case) has its closest neighbor at a distance smaller than r0 (shaded area), then i is removed. This removal condition is checked synchronously for all nodes at once, hence node j in the sketch is also removed because, since the network is undirected, i is a neighbor at a distance smaller than r0. In (b), the size of the giant connected component is a function of r0. The interaction radius is set to r = 0.1, above which links cannot be drawn, and kept the same for all simulations. Different system size N are explored, indicated in the legend. Solid lines correspond to the theoretical approximation from Eq. (17) and markers are results from simulations. In (c), a discrepancy between theory and simulations, Eq. (18), as a function of the system size. All simulation points are averaged over 100 independent realizations.
Features related to a dynamical process
As a final application of the feature-enriched percolation, we investigate the case in which the features are coupled to dynamics running on top of the network. There are many situations in which the dynamical evolution of some processes on the network generates some quantity, or attribute, that might not be evenly distributed across nodes. For instance, when studying the problem of synchronization, it is known that in the desynchronized phase, the synchronization error—the time-averaged distance in the phase space between the state of a node and the average state of the system—displays a power-law decrease with the degree50. In such a scenario, one might be interested to study what is the surviving network after the removal of the most (or least) synchronized nodes with respect to the mean activity of the system. Another example is found in communication networks when modeling traffic, where nodes with a higher degree tend to be more congested on average51.
Here we focus on the SIS model, well-known in the context of epidemiology52. It consists of nodes that can be in either of two states, susceptible or infected. Infected nodes transmit the disease to susceptible ones at a certain rate upon encounter, and infected nodes recover spontaneously at a different rate. The dynamical evolution of the model is written as
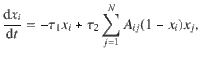
For certain dynamical processes on certain types of topologies, one can calculate the exact joint degree-feature distribution and plug it into Eqs. (1)– (5). However, these will be marginal cases over all the ensemble of dynamical models and network architectures, and for many applications, the joint distribution will not be analytically available. To illustrate how one can proceed in this latter case, here we take an agnostic approach and use only information about the node degrees and their feature value to infer an approximate P(k, F). We first collect all the pairs (ki, Fi) and compute a non-normalized two-dimensional histogram, see Fig. 5a. The collapse in the k − F plane tells us the type of correlation between degree and feature, that for the case of the SIS turns out to be positive. Note that for each value of the degree (recall that k is considered discrete), the distribution P(F∣k) has a bell-shape curve, of different height, different mean value, and different width, see the ridgeline plot of Fig. 5b for a better appreciation. The first strong approximation is to consider that each P(F∣k) is proportional to a normal form
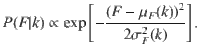
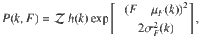

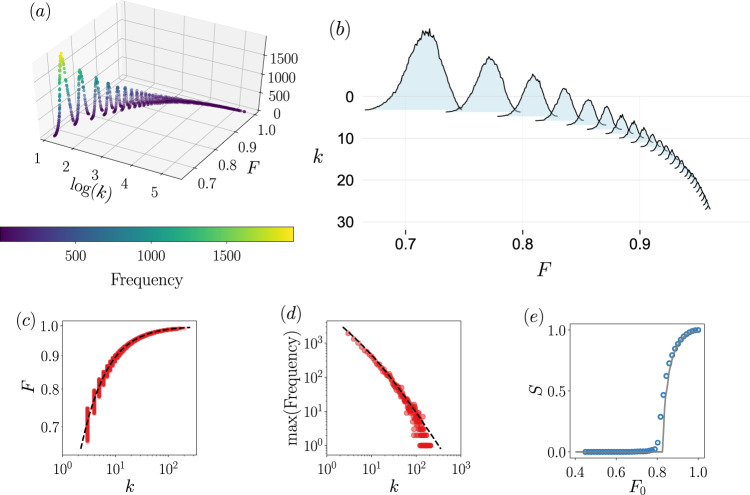
Feature-enriched percolation of the SIS model.
We integrate the dynamical Eq. (19) for a reshuffled Barabási–Albert70, with m = 3 and system size N = 2000. A non-normalized histogram of the pairs (ki, Fi), where the feature value is Fi = xi(t → ∞), is shown in (a). The input data for the histogram comes from 100 independent realizations. In (b), ridge plot of the 25 first curves of the histogram, i.e., those with the lowest degree and highest peaks. The bell shape behavior with varying mean, standard deviation, and peak height can clearly be appreciated. In (c), projection of the k − F plain, together with the expressions μF(k) (see text) given by the Bayesian machine scientist method. The standard deviation σF(k) is not shown because it visually overlaps μF(k) for large k. The expressions are
In Fig. 5e we compare the results of the simulations with the curve obtained from the theory. We have employed the joint degree-feature distribution (21) to compute the generating functions, but we proceed numerically because no closed expressions can be found. We see that the agreement is quite good, despite the strong approximations used during the process. A small discrepancy around the critical region can be appreciated, rooted in finite-size effects and probably a systematic deviation that could potentially be reduced by employing more complicated functions in the process of constructing P(k, F), such as skewed Gaussian distributions. Anyway, we have shown that with little information one can find a quite satisfactory description of the percolation properties of systems in which the features are related to a dynamical process. This works reasonably well for synthetic networks, and we proceed next to test the accuracy of the feature-enriched percolation in real networks, which are characterized by topological correlations not taken into account in the theory.
To this goal, we use three different dynamics on three different real networks and proceed similarly as before, i.e., we will find the approximate degree-feature joint distribution by means of the BMS. The first example is a mutualistic dynamics arisen in symbiotic ecosystems, where the time dependence of the abundance xi of the species i is given by the equation54,55
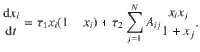

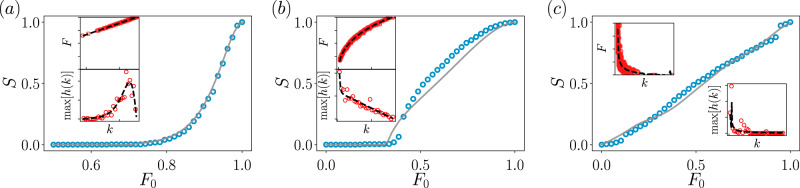
Feature-enriched percolation of dynamical processes on top of real-world networks.
In (a) mutualistic dynamics are given by Eq. (22), in (b) population dynamics from Eq. (23) and in (c) the biochemical dynamics (24) The main plots display the size of the largest connected component from simulations (markers) and its approximation given by the theory (lines). Insets show the data used to feed the Bayesian machine scientist (markers) and the resulting curves (dashed lines), used to calculate the degree-feature joint distribution (21). The output functions of the BMS are given in Supplementary Note 8. The feature is the value of the dynamical variable xi at the steady-state, normalized by its maximum value, i.e.,
The second example corresponds to birth-death processes57. In the context of population dynamics, the temporal evolution of the population xi in a site i can be described by
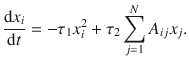
As a final dynamics, we use the mass-action kinetics model often employed in biochemistry58. The equation
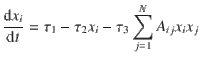
The dynamical processes presented here are merely illustrative examples of the potential and flexibility of the theory. For all the chosen examples the microscopic rules and the time evolution of the variable of interest were known, but we could have proceeded even without that information. There are two minimal ingredients to apply the feature-enriched percolation: the degree and the feature value for every node. If for whatever reason, a relation between the feature and the degree cannot be obtained, one can always proceed by employing the BMS technique, or other methods whose goal is to provide closed-form equations from data60–62.
Discussion
In recent years there has been an upsurge of contributions aiming at offering more realistic descriptions of the natural and socio-technical phenomena that networks encode, e.g., via multilayer63,64 or temporal65 networks, or via higher-order interactions66. These topological generalizations induce non-trivial consequences in network dynamics, with important implications for the stability and proper functioning of the systems when subjected to perturbations. Beyond these more accurate topological characterizations, there is a dimension that has been frequently ignored in the study of robustness and resilience, which is node metadata. Its omission is not rooted, by no means, in its irrelevance, but because node metadata is a type of information that many times is lost or disregarded in the process of constructing the networked architecture from empirical observations.
Taking percolation as the paradigmatic model to assess the robustness of a network, in this article, we propose a natural generalization of this phenomenon, flexible enough to include node removal protocols based on a combination of the degree and non-topological node metadata, what we call the features. We have worked out the analytical expression for the size of the giant component and have checked its good agreement with simulations. We have discussed in some detail the phenomenology that appeared in a set of examples displaying typical degree-feature relations of real systems, such as the critical exponents of the transition or the characterization of the non-monotonic response of the robustness induced by the correlations. In this first part of the article, the nature of the features has been left undetermined and, far from being a limitation, this is actually a strength of our model. Indeed, the origin of real node metadata can be either an exogenous or endogenous property of the nodes, can be either of constant or mutable nature, can be either numerical or non-numerical, etc. All these cases can be included in our model. In the second part of the article, we have dealt with two families of problems in which the features have a physical meaning: spatial networks and dynamical processes on networks. The latter case is the most challenging problem because very frequently one cannot analytically extract the main ingredient to use the feature-enriched percolation framework, the joint degree-feature distribution. We have shown, however, how to overcome this limitation by employing a state-of-the-art probabilistic method that gives us an approximate distribution.
A groundbreaking discovery in network robustness assessments was the realization that the response to random failures and degree attacks is radically different when the variance of the degree distribution is much larger than the mean degree. We believe that, in a similar vein, conceptualizing the possibility of attacking networks with new feature-based protocols, and providing the mathematical framework to study this process, can help unravel unexpected responses and hidden fragilities. We hypothesize that it might be possible to choose a smart occupation probability ϕk,F that leads to a truly discontinuous percolation phase transition, thus identifying a crucial subset of nodes (that is, from a network ensemble perspective, identifying the range of degree and feature values) that once removed cause catastrophic consequences for the robustness of the system.
Because our model builds upon traditional, well-grounded message-passing techniques that have been successfully employed in a myriad of different problems, many generalizations not treated in the present work are still possible. Some of them are the study of bond percolation based on features, which is a very relevant situation because many existing network datasets convey information about the link weight rather than node metadata. Generalizations are also possible in topologically correlated networks, i.e., those showing clustering or non-trivial assortativity mixing. Percolation in multilayer networks has also attracted a considerable extent of attention in the last decade, and feature-based protocols can be devised in these layered structures as well. The feature dimension can be relevant too when studying optimal percolation, that is, finding the sets of nodes that, when removed, cause the largest possible reduction in the giant component. Indeed, one can devise attacks that combine feature and topological information, more complex than the one studied in this article, in order to eventually outperform purely topologically-based interventions and move closer to the optimal dismantling. Finally, a conceptually similar problem but that would require a completely different mathematical approach is the one of feature-based percolation in low-dimensional lattices, where it can be addressed which traits of the feature distribution modify the well-known properties of these systems.
Last, but not least, we would like to discuss some implications of our model on the robustness of complex interconnected systems. Firstly, we are opening the doors to the possibility of assessing the behavior of a network as a function of the combination of several traits, enabling the exploration of responses in large phase spaces. This can be particularly useful not only for scientific research problems but for policy making too, where, many times, it is needed to evaluate scenarios taking into account the optimization of a multitude of factors. Think, for instance, in the current COVID-19 pandemic, where policies have required to maintain a delicate balance between the protection of public health and the sustainability of the economic system. Our model represents a first step towards the non-topological multidimensional optimization of robustness. Secondly, depending on the nature of the features, different implementations can be devised. There are some situations in which the features values can be tuned at will, e.g., resources are given to certain nodes, therefore it can be explored how to modify the feature allocation, correlating it with topological information, in order to better protect the network. We learned, for instance, that the robustness in networks with positively correlated degree-feature distributions is considerably lower than a network with uncorrelated degree-feature, and that this is not always true for negatively correlated ones. This kind of information can be exploited, of course combining it with attacking protocol. There are other situations in which the features remain fixed, e.g., the age of nodes, but the topology is flexible. Put otherwise, we can tune the strength of correlations at will by redirecting the edges in a convenient way. Here we can also take advantage of the relation between correlation and robustness to increase the system’s ability to sustain its function despite the attacks. Finally, we can also use our formalism to infer the temporal evolution of the robustness in the case where the features evolve. For the sake of illustration, in the article, we have presented several examples of dynamics with well-defined equations that display a steady state, but none of these characteristics are actually necessary. It just suffices to have an accurate prediction for the future feature values, whatever the way we have used to obtain it. Taking snapshots at different times, we can apply the BMS method at each of them to obtain a time-dependent size of the largest connected component. This allows us to gain access to information on when a system will be most robust and most vulnerable, hence forestalling undesired behaviors. All these practical examples evince the potential of our framework, from which insightful lessons can be learned to better protect, or dismantle real systems. Likewise, at a fundamental level, a very interesting new phenomenology can be obtained due to the inclusion of features. For all these reasons we hope our model becomes a stepping-stone on the path towards a more realistic and useful description of the process of network robustness.
Supplementary information
The online version contains supplementary material available at 10.1038/s41467-021-22721-z.
Author contributions
O.A. performed the analytical computations and the simulations. O.A. and M.D.D. designed the research, discussed and interpreted the results, and wrote and revised the manuscript.
Data availability
All datasets used in this article are publicly available on the Internet. The data used in Fig. 1a can be found at https://zenodo.org/record/3553442. The data used in Fig. 1b can be found at https://consonni.dev/datasets/. The data used in Fig. 1c can be found at https://covid19obs.fbk.eu/#/api. The data used in Fig. 6a, b can be found at https://iwdb.nceas.ucsb.edu/html/robertson_1929.html. The data used in Fig. 6c can be found at http://interactome.dfci.harvard.edu/C_elegans/index.php?page=download.
Code availability
The code for the Bayesian Machine Scientist is available at https://bitbucket.org/rguimera/machine-scientist/. Another code relevant to the paper is available from the authors upon reasonable request.
Competing interests
The authors declare no competing interests.
References
1.
2.
3.
4.
5.
6.
7.
8.
9.
10.
11.
12.
13.
14.
15.
16.
17.
18.
19.
20.
21.
22.
23.
24.
25.
26.
27.
28.
29.
30.
31.
32.
33.
34.
35.
36.
37.
38.
39.
40.
41.
42.
43.
44.
45.
46.
47.
48.
49.
50.
51.
52.
53.
54.
55.
56.
57.
58.
59.
60.
61.
62.
63.
64.
65.
66.
67.
68.
69.
70.
 Percolation on feature-enriched interconnected systems
Percolation on feature-enriched interconnected systems
