
- Altmetric
Quantum random numbers distinguish themselves from others by their intrinsic unpredictability arising from the principles of quantum mechanics. As such they are extremely useful in many scientific and real-world applications with considerable efforts going into their realizations. Most demonstrations focus on high asymptotic generation rates. For this goal, a large number of repeated trials are required to accumulate a significant store of certifiable randomness, resulting in a high latency between the initial request and the delivery of the requested random bits. Here we demonstrate low-latency real-time certifiable randomness generation from measurements on photonic time-bin states. For this, we develop methods to certify randomness taking into account adversarial imperfections in both the state preparation and the measurement apparatus. Every 0.12 s we generate a block of 8192 random bits which are certifiable against all quantum adversaries with an error bounded by 2−64. Our quantum random number generator is thus well suited for realizing a continuously-operating, high-security and high-speed quantum randomness beacon.
In quantum random number generation, one has generally to choose between high speed and strong security. Here, the authors show how to bound several adversarial imperfections on state preparation and measurement, generating 8192 secure random bits every 0.12 s in real time using a simple apparatus.
Introduction
Quantum mechanics is well known to offer many opportunities for generating genuine randomness that is unpredictable by any reference1–3. This unpredictability can be proven based only on measurement observations and a few assumptions. Therefore, the randomness generated according to quantum mechanics is certifiable. The simplest example involves measuring a two-level quantum system (a qubit) prepared in an equal superposition of its two levels. However, its proper working and certifiability rely on the trust of both the quantum state prepared and the measurement performed. This scheme is thus device-dependent2,3. On the other hand, there are also device-independent schemes that do not require any trust on the inner working of the employed quantum devices4,5. Unfortunately, it is difficult to realize such a scheme for practical use with excellent performance as it requires a loophole-free Bell test6–11. Consequently, the randomness-generation rates achieved are extremely low with a high latency from the beginning of the experiment to the output of the certified random bits12–15. The natural question then is whether we can reduce the trust required by the above simple scheme while avoiding the difficulties inherent in the device-independent approach.
In this work we explore a simple practical scheme for the realization of a low-latency real-time certifiable quantum random number generator (QRNG). The simple scheme works ideally as follows: At each trial a horizontally polarized single photon is emitted from a source, and then measured randomly along either the X-basis (diagonal/anti-diagonal polarization basis) to generate a random bit or the Z-basis (horizontal/vertical polarization basis) to verify the prepared state. This scheme is motivated by that for entanglement-based quantum key distribution (QKD)16,17, where one basis is used to generate secret keys and other bases are used to estimate the prepared state. Random bits or secret keys can be certified since measurement outcomes allow us to bound the correlation between the prepared state and the side information of an adversary known as Eve18.
The above ideal scheme has been well studied in the literature19,20. However, in order to make the resulting QRNG practical, we need to consider the imperfections in its implementations and show the robustness of randomness generation against those imperfections. First, single-photon sources are not easily accessible and as for QKD18, weak optical pulses are usually employed. Even if a single-photon source is available, it is still generally difficult to produce a particular quantum state with high accuracy. Second, it is difficult in an experiment to perform measurements precisely along both the X-basis and Z-basis, as one basis tends to be more precise than the other. Third, the basis choice at a trial is usually made by a pseudo or physical random number generator. This means that the probabilities of selecting the X-basis and Z-basis, denoted as PX and PZ, can only be bounded but not exactly known. Furthermore, in the adversarial scenario Eve could manipulate these imperfections. These adversarial imperfections must be addressed together to reliably certify randomness which currently has not been done.
Here we develop a method to guarantee the proper working and security of our QRNG in the presence of those above adversarial imperfections. For this, we require a lower bound q1,lb on the single-photon probability in a practical photon source (such as a weak laser pulse in the absence of a phase reference), an upper bound δ on the misalignment angle between the X-basis and Z-basis, and both a lower and an upper bounds on the imbalance between the probabilities PX and PZ given by τ = (PX − PZ)/2. We emphasize that except the above bounds which characterize the adversarial imperfections, our method does not need any other information about the state prepared or measurements performed. In this sense, our QRNG works in a semi-device-independent way. The values of the above imperfection bounds can be obtained by calibrating the photon source and measurement apparatuses in real time. We allow Eve to manipulate the state prepared or measurements performed as long as these manipulations satisfy the above imperfection bounds. Our method is of excellent finite-data efficiency, thus enabling low-latency real-time randomness generation. Specifically, we experimentally demonstrate that every 0.1 s a sufficient amount of entropy with respect to the quantum (or classical) side information of Eve is certified such that a block of 8192 (or 2 × 8192) random bits is generated with a certified error bounded by 2−64 and with an extraction time of 0.02 s (or 0.04 s).
Results
Outline
In what follows, we first introduce the setup of the problem and the main idea of our method for certifying randomness with the adversarial imperfections discussed above. Our method works in the presence of both the classical and quantum side information of Eve. We then illustrate the performance of our method with simulations, showing the advantage of Eve with an access to quantum side information. Finally, we present our experimental realization of a simple low-latency real-time QRNG enabled by our method.
Setup of the problem
To generate random bits, we consider an experiment with a sequence of n repeated trials. These trials are not necessarily independent or identical. We denote the input (basis choice) and the output (measurement outcome) at the k’th trial by the random variables Ik and Ok, respectively. The inputs and outputs of the experiment are then and
For certifying the randomness in the outputs On relative to the inputs In and Eve, we must assume that the outputs On are kept private and not accessible to Eve. We allow Eve to hold classical or quantum side information about the state prepared at a trial. At the same time, we allow Eve to manipulate the distribution of the possible inputs and the specific forms of the associated measurements at the trial, as long as these manipulations satisfy the prespecified imperfection bounds. We assume that by manipulations Eve can access classical side information but not quantum side information about the measurement performed. The method to be presented allows classical correlations between Eve’s side information about the state prepared and Eve’s partial knowledge of the input and measurement used at each trial. That is, the state prepared can be classically correlated with the input selected or the measurement performed. We emphasize that our method cannot be applied in the case where at each trial Eve’s side information about the state is correlated in a quantum manner with Eve’s partial knowledge of the input and measurement. Moreover, although we allow Eve to manipulate the input distribution, we assume that before a trial Eve has no perfect knowledge of which specific input to be selected at the trial. This assumption is required for security analysis; otherwise, Eve can deterministically forecast the output of the trial, and it would be therefore impossible to certify randomness24.
Main idea of our method
For certifying randomness with respect to classical and quantum side information, we construct probability estimation factors (PEFs)25,26 and quantum estimation factors (QEFs)27,28, respectively. Both a PEF and a QEF are non-negative functions of the input I and output O of a trial, denoted by Fc(I, O) and Fq(I, O). The key observation is that the smooth conditional min-entropies
After certifying the amount of randomness, we run the randomness extractor developed in ref. 29 with extractor error ϵx = ϵ − ϵs in order to generate random bits which are within distance of ϵ > ϵs from uniform. The distance ϵ is termed the soundness error. For the results presented in this work, we set the smoothness error and the extractor error to be ϵs = 0.8ϵ and ϵx = 0.2ϵ.
Advantage of quantum adversaries over classical adversaries
We illustrate with simulations the performance of our method in the asymptotic limit, so that one can see the expected behavior of our QRNG scheme. When the trials are identical and n approaches infinity, the amount of randomness certified by our method increases linearly with n. The increasing rate (per trial) is called the asymptotic randomness-generation rate. The rates in the presence of classical and quantum side information, Rc and Rq, certified by our method are optimal (see refs. 25,27 for general proofs). We can quantify Rc and Rq as functions of the depolarization noise d (as defined in the caption of Fig. 1). The results presented in Fig. 1 clearly indicate that Eve’s access to quantum side information as compared with classical side information results in a reduction of the randomness-generation rate. Such a reduction is an important yet unquantified advantage to Eve.

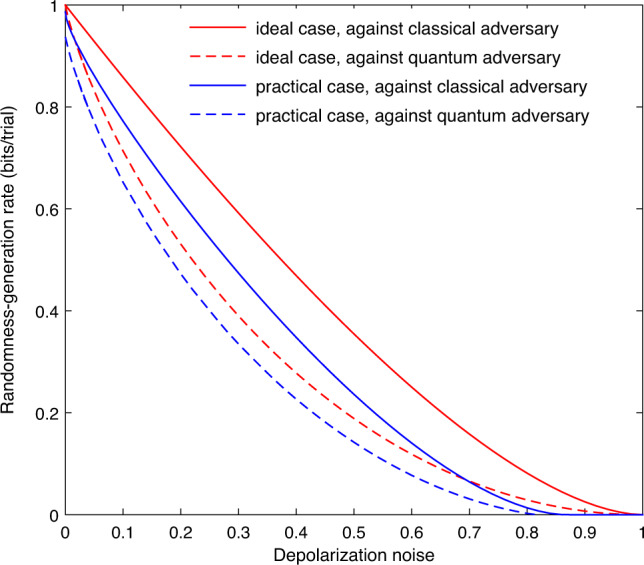
Asymptotic randomness-generation rates Rc and Rq as functions of the depolarization noise d.
For illustration purpose, here we simulate the result at a trial according to either the X-basis or Z-basis measurement on the depolarized single-photon state
Experimental realization of a simple low-latency real-time QRNG
To realize a QRNG, we perform measurements on photonic time-bin states, where the quantum information is encoded into the superposition of two different temporal positions (time bins) of an optical pulse. The two time bins are usually called the early and late time bins denoted by te and tl. Time-bin encoding has been widely used especially in fiber-based quantum communication systems30. The advantage of time-bin encoding lies in that both the state source and the measurement apparatus required are easily packaged onto a chip, which is an important factor to consider for practical QRNG use.
To produce randomness, at each trial we attempt to prepare the time-bin qubit state

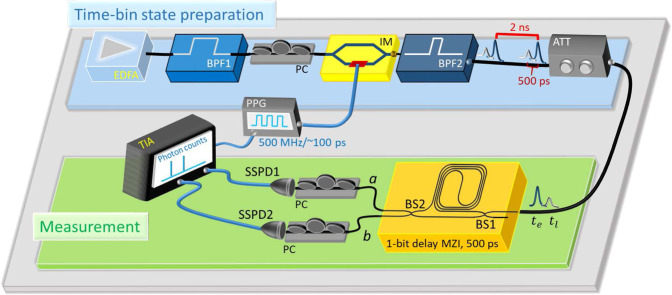
Schematic diagram of our experimental setup.
First, the time-bin state
In practice, the source emits zero photon with a non-zero probability at each trial, and threshold detectors (which cannot resolve photon number) of finite efficiency are employed. Moreover, a photon can be lost over the transmission from the source to the detectors. Therefore, not all trials have detector clicks. For security analysis, we assume that the trials with detector clicks are a fair sample of all trials. Accordingly, no-click events do not affect the security analysis of randomness generation but only the rate and latency achieved in practice.
Now for certifying randomness, we must take into account the adversarial imperfections in our setup. Neither of the two beam splitters, BS1 and BS2, in the MZI has the ideal 50:50 splitting ratio. In addition, the two detectors at the output ports a and b may have different efficiencies ηa and ηb. These facts induce not only an imbalance between the probabilities PX and PZ of selecting the X-basis and Z-basis but also a misalignment between the two bases. Based on a calibration of our measurement apparatus, we found that the splitting ratios of BS1 and BS2 are 53.8:46.2 and 46.9:53.1, respectively, and that the ratio ηa: ηb is 1.024:1. Consequently, the imbalance τ = (PX − PZ)/2 and misalignment δ satisfy the conditions ∣τ∣ ≤ 0.041 and δ ≤ 3.565∘. Moreover, we estimated that the single-photon component of the optical pulse contributes at least 99.3% of all click events. More details behind the above characterizations are available in Supplementary Note 3. Accordingly, we conservatively assume that ∣τ∣ ≤ 0.06, δ ≤ 6∘, and q1,lb = 0.98 in our security analysis, specifically, for constructing PEFs and QEFs to guarantee certifiable randomness generation.
Based on a set of calibration data, we estimated the expected number, kexp, of random bits certifiable every 0.1 s runtime at a soundness error ϵ varying from 10−5 to 10−30. The dependence of kexp on ϵ in the presence of either quantum or classical side information is illustrated in Fig. 3. As expected fewer number of random bits can be certified with respect to quantum side information than with respect to classical side information. However, the number of certifiable bits in each situation is not significantly affected by the soundness error in the range considered.

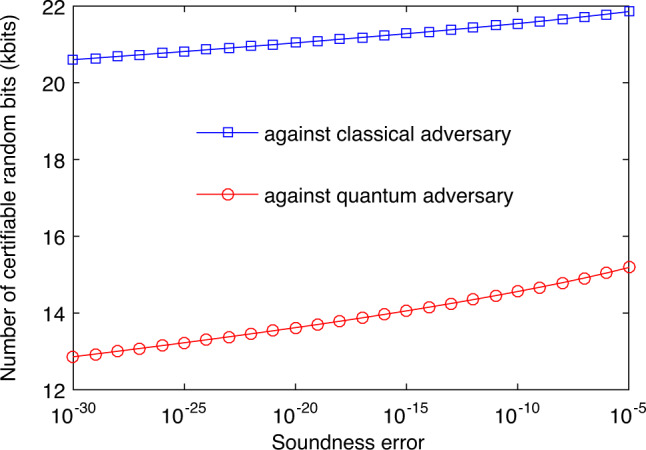
Trade-off between the soundness error ϵ and the expected number of random bits certifiable from the measurement outcomes observed every 0.1 s runtime.
The results in the presence of classical and quantum side information are shown as the blue and red curves, respectively.
We finally consider a request for a block of 8192 (or 2 × 8192) random bits in the presence of quantum (or classical) side information and with soundness error bounded by 2−64 ≈ 5.42 × 10−20. The results in Fig. 3 strongly suggest that our QRNG can successfully fulfill the request every 0.1 s runtime. Indeed, the success probability is estimated to be at least 1 − 2−380 (or 1 − 2−478) in the presence of quantum (or classical) side information (see Supplementary Note 4 for details). We further demonstrate this repeated fulfillment in experiment. For this, before the experiment we fixed the PEF and QEF used, as well as several other parameters used in our security analysis, based on the above calibration data (see Supplementary Note 4). Then we ran the experiment for 420 s and processed the data block obtained every 0.1 s runtime successively. For each data block, we certified a lower bound on the number of random bits extractable with soundness error 2−64 and with respect to either quantum or classical side information. If the certified lower bound exceeds the request threshold, the instance of our QRNG succeeds. Conditional on success, we run the randomness extractor developed in29 to generate the final random bits. The randomness extractor is seed-efficient and requires an additional processing time: for extracting 8192 (or 2 × 8192) random bits it takes 0.02 s (or 0.04 s), respectively. Totally we ran 4200 instances of our QRNG. The analysis results summarized in Fig. 4 show the success of each instance.

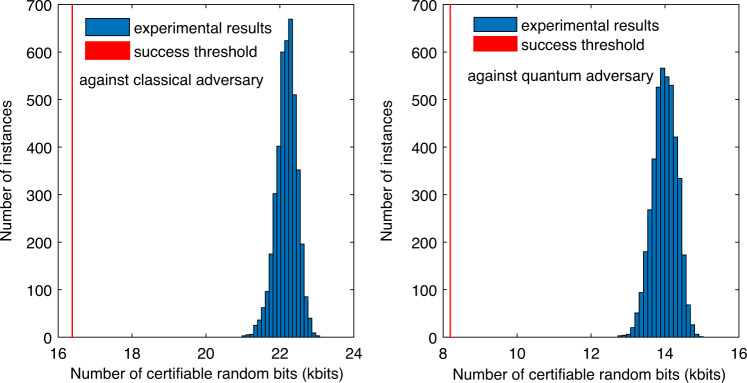
Histogram of the numbers of random bits certifiable with soundness error 2−64 from 4200 instances of our QRNG: the left and right panels are for certifying randomness with respect to classical and quantum side information, respectively.
Each instance of our QRNG uses a data block obtained in 0.1 s runtime. In each panel, the experimental results are shown as blue bars, while the success threshold is shown as the red line.
Discussion
In conclusion, we demonstrate a simple low-latency real-time certifiable quantum random number generator (QRNG). The generator is based on the measurement of a weak optical pulse with an unbalanced Mach-Zehnder interferometer. By developing an efficient security-analysis method, genuine randomness can be certified and then generated with a low latency from every short block of experimental data even at an extremely high security level and even considering adversarial imperfections in our experimental setup. Further, the implementation of randomness extraction allows real-time performance to be achieved. Our QRNG is thus well suited for realizing a continuously-operating, high-security, and high-speed quantum randomness beacon.
Our security analysis considers both quantum and classical side information. Our security certificate is resistant to the adversarial imperfections in both the state source and the measurement apparatus, in contrast to those certificates achieved in previous works20,32–34 where either the adversarial imperfections in the source or those in the measurement apparatus are considered. Moreover, our method exhibits unsurpassed finite-data efficiency. As certifying smooth conditional min-entropies is also the central task for quantum key distribution (QKD), we envision that our method can be extended to improve the finite-data efficiency of QKD. In the future work, we will address the details required for this extension.
Methods
Outline
Here we provide details of our experimental setup for realizing a simple low-latency real-time certifiable quantum random number generator. We also introduce the general framework of probability estimation (or quantum probability estimation) for certifiable randomness generation in the presence of classical (or quantum) side information. Further, we discuss the details of implementing these general frameworks in the presence of the adversarial imperfections considered in both the state source and the measurement apparatus.
Experimental implementation
Our experimental setup is shown in Fig. 2. To generate time-bin states, amplified spontaneous emission from an erbium-doped fiber amplifier (EDFA), which has a broad spectrum and thus can be regarded as inherently dephased, is used as a light source. After reducing its bandwidth by a band-pass filter (BPF1) of 1551.1 ± 1.2 nm, the light from the EDFA is sent into an intensity modulator (IM) to generate (in the ideal case) the time-bin qubit state consisting of the single-photon pulse
Certifiable randomness generation in the presence of classical side information
To certify randomness with respect to the classical side information of Eve, we apply the framework of probability estimation as developed in refs. 25,26. For this, we need to characterize each trial of the experiment by a classical model. In the scenario of our interest, the model is adapted to the adversarial imperfections considered. Given the model, we construct probability estimation factors (PEFs) which can certify randomness with respect to classical side information. Below we first introduce the concepts of classical models and PEFs, and then present the main result of probability estimation for randomness generation.
Let us focus on a generic trial in the experiment with an input I and an output O. We omit the trial index for generic trials. As is conventional, we denote a random variable and its possible value by an upper-case letter in regular math font and the corresponding lower-case letter. The classical side information E of Eve can be correlated with the trial input I and trial output O. This correlation is described by a joint probability distribution
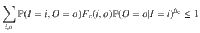
The number of near-uniform random bits extractable from the outputs On given the inputs In and the classical side information E of Eve is quantified by the classical smooth conditional min-entropy
Theorem 1 (Theorem 1 of ref. 26): Let 1 ≥ κ, ϵs > 0 and 1 ≥ p ≥ 1/∣Rng(On)∣, where ∣Rng(On)∣ is the number of possible outputs after n trials. Define Φ to be the event that Tc,n ≥ 1/(
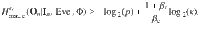
The event Φ can be interpreted as the event that the experiment succeeds. When the experiment succeeds, we compose the classical smooth conditional min-entropy bound in Eq. (2) with a classical-proof strong extractor of error ϵx (in total-variation distance), in order to obtain random bits which are within soundness error (in total-variation distance) ϵ = ϵs + ϵx from uniform in the presence of classical side information. See Sect. IV C of ref. 25 for the details of the end-to-end randomness generation. Note that an extractor is strong if the joint of its output and the seed is nearly uniform, while an extractor is classical-proof if it works in the presence of classical side information. In our experiment, we used Trevisan’s extractor36 as implemented by Mauerer, Portmann, and Scholz29, which we refer to as the TMPS extractor. The TMPS extractor is an efficient classical-proof strong extractor that requires few seed bits29,36. The way of running the TMPS extractor for our case is the same as for the case of device-independent randomness generation with respect to classical side information studied in refs. 13,25.
Certifiable randomness generation in the presence of quantum side information
To certify randomness with respect to the quantum side information of Eve, we apply the framework of quantum probability estimation as developed in refs. 27,28. For this, we need to characterize each trial of the experiment by a quantum model. In the scenario of our interest, the model is adapted to the adversarial imperfections considered. Given the model, we construct quantum estimation factors (QEFs) which can certify randomness with respect to quantum side information. Below we first introduce the concepts of quantum models and QEFs, and then present the main result of quantum probability estimation for randomness generation.
Consider a generic experimental trial which has a classical input I and a classical output O. Suppose that Eve holds a quantum system
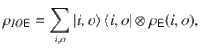
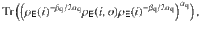
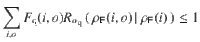
The number of near-uniform random bits extractable from the outputs On given the inputs In and the quantum side information carried by the system
Theorem 2 (Theorem 3 of ref. 28): Let 1≥κ, ϵs, p > 0. Define Φ to be the event that
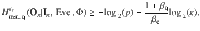
The event Φ can be interpreted as the event that the experiment succeeds. When the experiment succeeds, we compose the quantum smooth conditional min-entropy bound in Eq. (6) with a quantum-proof strong extractor of error ϵx (in trace distance), in order to obtain random bits which are within soundness error (in trace distance) ϵ = ϵs + ϵx from uniform in the presence of quantum side information. See Sect. V of ref. 28 for the details of the end-to-end randomness generation. Note that an extractor is quantum-proof if it works in the presence of quantum side information. As the TMPS extractor29,36 is a quantum-proof strong extractor37, we use this extractor for randomness extraction. The way of running the TMPS extractor for our case is the same as for the case of device-independent randomness generation with respect to quantum side information studied in refs. 15,27,28.
Constructions of PEFs and QEFs with adversarial imperfections
Both probability estimation and quantum probability estimation are general frameworks for certifying randomness; however, their implementations are case-dependent as both the classical and quantum models for a trial depend on the case of interest. For the case of device-independent randomness generation, both frameworks have been implemented, see refs. 15,25–28. In this work we would like to apply probability estimation and quantum probability estimation for randomness generation with partially characterized quantum devices. For this, we need to first construct the classical model
To construct the models
To construct the sub-models
On the other hand, when multiple photons are emitted (i.e., j > 1) we construct the sub-models
Once the classical model
Reporting summary
Further information on research design is available in the Nature Research Reporting Summary linked to this article.
Supplementary information
The online version contains supplementary material available at 10.1038/s41467-021-21069-8.
Acknowledgements
We thank Emanuel Knill for stimulating discussions and Ivan Iakoupov for help with running the extractor. This work includes contributions of the National Institute of Standards and Technology, which are not subject to U.S. copyright.
Author contributions
Y.Z. and H.P.L. contributed equally to this work. Y.Z., H.T., H.P.L., and W.J.M. conceived the original concept and proposed the experiment, which was carried out by H.P.L. together with T.I. and T.H. Y.Z. developed the security-analysis method and conducted the data analysis. The randomness extraction was preformed by Y.Z. and A.M. All authors discussed the results and contributed to the writing of the paper.
Data availability
The data that support the findings of this study are available from the corresponding authors upon reasonable request.
Code availability
The code that produces the results presented in this work is available from the corresponding authors upon reasonable request.
Competing interests
The authors declare no competing interests.
References
1.
2.
3.
4.
5.
6.
7.
8.
9.
10.
11.
12.
13.
14.
15.
16.
17.
18.
19.
20.
21.
22.
23.
24.
25.
26.
27.
28.
29.
30.
31.
32.
33.
34.
35.
36.
37.
38.
39.
 A simple low-latency real-time certifiable quantum random number generator
A simple low-latency real-time certifiable quantum random number generator
