
Competing Interests: The authors have declared that no competing interests exist.
- Altmetric
The location-based services can provide users with the requested location information. But users also need to disclose their current location to the location-based service provider. Therefore, how to protect user’s location privacy is a major concern. In this paper, we propose a heterogeneous deniable authenticated encryption scheme called HDAE for location-based services. The proposed scheme permits a sender in a public key infrastructure environment to transmit a message to a receiver in an identity-based environment. Our design utilizes a hybrid encryption method combing the tag-key encapsulation mechanism (tag-KEM) and the data encapsulation mechanism (DEM), which is well adopted for location-based services applications. We give how to design an HDAE scheme utilizing a heterogeneous deniable authenticated tag-KEM (HDATK) and a DEM. We also construct an HDATK scheme and provide security proof in the random oracle model. Comprehensive analysis shows that our scheme is efficient and secure. In addition, we give an application of the HDAE to a location-based services system.
Introduction
The fast expansion of smart devices and mobile networks makes location-based services (LBSs) an integral part of people’s daily lives. Users utilize LBSs to find points of interests, navigate the destination, and inquire public transportation etc. [1–6]. In all of these requested services, users need to disclose their location information to the location-based service provider (LBSP). Based on location information, LBSP is able to infer some sensitive information about users, such as preferences, social circles, and trajectories. For example, if a user frequently presents location request to the same hospital, the LBSP is able to deduce that the user may have a physical issue.
If the LBSP cooperates with a malicious adversary for pecuniary advantage, there will be significant loss of profits for users. For example, based on the location-based privacy information leaked by a user, a malicious adversary can infer a user’s home address or routine and then commit theft, which seriously threatens user’s personal and property safety. Therefore, protecting users’ location privacy is a major concern.
Authentication plays a very important role in the LBS [7–16]. Only authorized users can access the LBS. Typically, we utilize digital signature technology to achieve authentication. However, there is also non-repudiation in digital signature. That is, the sender cannot deny the message he/she signed. To resolve this issue, deniable authentication [17] is proposed which has two characteristics: (1) the receiver has the capability of identifying whether a given message is from the sender; (2) any third party is incapable of determining whether the given message is from the sender or the receiver even though the third party colludes with the receiver since the receiver is able to generate a probabilistically indistinguishable transcript from the sender. However, in privacy-preserving scenarios, the transmitted message needs to be encrypted to achieve confidentiality. Wu and Li [18] first presented an identity-based DAE scheme to achieve confidentiality as well as deniable authentication in an efficient approach.
0.1 Motivation and contribution
In order to make the designed scheme more practical, we require the sender and receiver to be in different cryptographic environments. Concretely, we design a heterogeneous deniable authenticated encryption (HDAE) scheme utilizing tag-KEM and DEM hybrid encryption methods. The proposed scheme permits a sender in a public key infrastructure (PKI) setting to deliver a message to a receiver in an identity-based cryptography (IBC) setting. This construction provides security proof in random oracle model (ROM) under the DBDH and BDH assumptions. Our experimental analysis displays that our scheme has a high efficiency and security. Additionally, we design an LBS scheme utilizing our proposed HDAE scheme. On the one hand, it permits the LBSP to affirm whether the ciphertext of the submitted location request is from the user. On the other hand, any third party cannot determine whether the ciphertext of the submitted location request is from the user or the service provider even though the third party colludes with the LBSP since the LBSP has the capability of generating a probabilistically indistinguishable ciphertext from the user.
0.2 Organization
The rest of this paper is arranged below. Section II, Related work is presented. Problem formulation is defined in Section III. We design a formal model for the HDAE in Section IV. Section V, a security model for the HDATK is depicted. An HDAE design is presented in Section VI, and we design an HDATK scheme in Section VII. Performance analysis is discussed in Section VIII. Section IX, we give an HDAE application to the LBS. Conclusion is drawn in Section X.
1 Related work
Related notions, hybrid encryption, deniable authenticated encryption, and heterogeneous deniable authentication are introduced.
Hybrid encryption constitutes a key encapsulation mechanism (KEM) and a data encapsulation mechanism (DEM). The KEM encrypts a session key by a public key, whereas the DEM encrypts the real data by a session key. For large messages, hybrid encryption is the best choice. Cramer and Shoup [19] designed practical and provably secure hybrid KEM/DEM schemes. Abe et al. [20] put forward to a more efficient tag-KEM/DEM scheme. Then, many KEM/DEM schemes [21–28] have been proposed. These designs support both components modular design. Sahai et al. [29] put forward to a tag-KEM/DEM scheme by a non-interactive proof method. The proposed scheme can encrypt message with arbitrary length. Baek et al. [30] presented a stateful KEM-DEM scheme. It is highly effective by utilizing a state to produce the random parameters.
Deniable authentication encryption (DAE) is a cryptographic primitive which can accomplish concurrently public key encryption and deniable authentication. Its cost is lower than that needed by deniable authentication-then-encryption manner. The DAE can achieve deniable authentication and confidentiality simultaneously which is well adopted for privacy-protecting scenarios.
Li et al. [31] constructed a DAE scheme with formal security proof. They also constructed an email system based on the designed DAE scheme. Jin et al. [32] constructed a DAE scheme which can realize simultaneously deniable authentication, confidentiality, and ciphertext anonimity. Rasmussen and Gasti [33] proposed a DAE based on two encryption schemes with strong and weak properties. Recently, Huang et al. [34] constructed a DAE scheme for privacy protection with formal security proof. The above mentioned schemes are all in the PKI environment which has public key management problems, including distribution, storage, and revocation. To resolve this issue, a number of identity-based deniable authenticated encryption (IBDAE) schemes have been constructed. Wu and Li [18] constructed an IBDAE scheme which provided formal security proof. Li et al. [35] (denoted by LZJ) proposed an IBDAE scheme for e-mail system. In their scheme, they utilize tag-KEM/DEM hybrid encryption technology which is more suitable for actual applications. Jin and Zhao [36] designed an IBDAE scheme which admitted formal security proof. The aforementioned schemes have key escrow problems, i.e., a third party called private key generator (PKG) knows all user’s private key. To avoid this problem, a certificateless deniable authenticated encryption (CLDAE) scheme [37] has been designed. Recently, Chen et al. [38] proposed a certificateless hybrid KEM/DEM scheme. It separates two parts to provide better security and efficiency.
The aforementioned DAE schemes have a common feature, i.e., the entities of these schemes are all in the same cryptosystem. Such characteristic makes these schemes not well suitable for the LBS system. Li et al. [39] (denoted by LHO) designed two heterogeneous deniable authentication (HDA) schemes. Their designed schemes allowed batch verification to accelerate the authenticators’ verification. Jin et al. [40] constructed an HDA scheme. In their scheme, a sender in a CLC setting delivered a message to a receiver in an IBC setting. However, these schemes do not achieve confidentiality.
2 Problem formulation
2.1 System and security models
There are three entities in the HDAE as shown in Fig 1: a user, an LBSP, and a trusted third party PKG. The location information and the corresponding ciphertext are produced by the user, and the ciphertext are sent to the LBSP. The LBSP can identify the received ciphertext is from the user and generate a probabilistically indistinguishable ciphertext from the user. The PKG is mainly responsible for generating system parameters and LBSP’s private key.

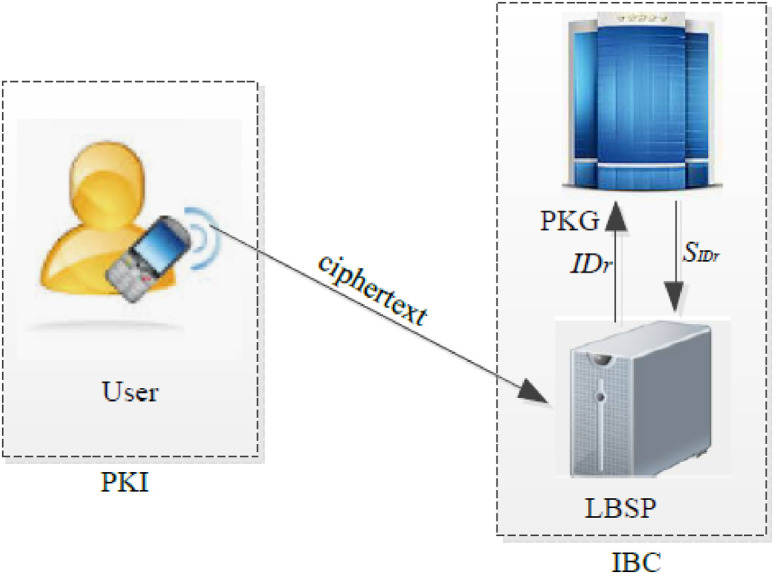
System model.
To obtain the location-based service that supports privacy-preserving, in the proposed system model, the user sends the ciphertext of location-requested information to the LBSP. Then the LBSP decrypts the received ciphertext and checks whether the decrypted message is location-requested information or a failure symbol ⊥.
2.2 Threat model and security goals
We define an adversary which will act as a user to learn the requested location information of other users. The LBSP is honest-but-curious. It means that it follows the designed scheme, but it may collude with a third party for economic benefits. Additionally, the collusion attack between the LBSP and a third party is concerned in the proposed security goals. Specially, two kinds of security requirements are considered in the constructed scheme.
Confidentiality: Any information about the submitted location information of a ciphertext cannot be learned by any third party other than the involved entities;
Deniable authentication: The LBSP has a capability of determining a ciphertext is from the user and creating a ciphertext that is probabilistically indistinguishable from the user.
3 PI-HDAE
We describe security notions for the HDAE in this section. In the designed HDAE scheme, a sender in a PKI environment, while a receiver in an IBC environment. PI-HDAE is denoted by this kind of DAE as follows.
3.1 Syntax
A PI-HDAE scheme comprises five algorithms below:
Setup: Given system parameter 1k, the PKG obtains the params and a master private key s. In other algorithms, we neglect params due to they are public.
PKI-KG: A user belongs to the PKI setting elects a secret key sk and calculates its public key pk.
IBC-KE: A user in the IBC setting transmits its identity ID to the PKG who computes its private key SID and securely passes it to the user. Here, let the user’s public key be its identity ID.
Deniable-Authenticated-Encrypt(DAE): Given a message m, a sender’s secret key sks, public key pks, and a receiver’s identity IDr, the sender obtains a ciphertext σ.
Deniable-Authenticated-Decrypt(DAD): Given a ciphertext σ, a sender’s public key pks, a receiver’s identity IDr, and its private key , the receiver obtains a message m or a symbol ⊥.
If σ = DAE(m, sks, pks, IDr), then m = DAD(σ, pks, IDr,
3.2 Security notions
We rewrite the notions [35] to meet our scheme. For confidentiality, the standard security concept, indistinguishability against adaptive chosen ciphertext attacks (IND-CCA2) is employed in our construction.
For IND-CCA2 security in a PI-HDAE scheme, it is assumed that this game below is between an adversary
“IND-CCA2” game (Game-I):
Setup.
Phase 1.
Key extraction queries:
DAE queries:
DAD queries:
Challenge.
Phase 2.
Guess.
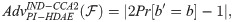
Definition 1. A PI-HDAE scheme is IND-CCA2 secure if there is a probabilistic polynomial time (PPT) adversary
In the aforementioned definition,
For deniable authentication, the security concept, deniable authentication against adaptive chosen message attacks (DA-CMA) is employed in our construction.
For DA-CMA in a PI-HDAE scheme, this game below is between
“DA-CMA” game (Game-II):
Setup. This is identical to Game-I.
Attack. This is identical to Game-I.
Forgery.
DAD(σ*,
Definition 2. A PI-HDAE scheme is DA-CMA secure if there is a PPT adversary
In the aforementioned definition,
3.3 Data Encapsulation Mechanism (DEM)
Two algorithms are included in a DEM.
Enc: Given 1k, a message m, and a key K, this algorithm outputs a ciphertext c. It is denoted as c = Enc(K, m).
Dec: Given a key K, and a ciphertext c, this algorithm outputs a message m or ⊥.
For a DEM, the security concept, indistinguishability against passive attackers (IND-PA) is employed in our construction. The game below is between
IND-PA game (Game-III):
Setup.
Challenge.
Guess.
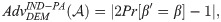
Definition 3. A DEM is DA-CPA secure if there is a PPT adversary
4 PI-HDATK
The security notions for heterogeneous deniable authenticated tag-KEM (HDATK) are given in this section. In the designed HDATK scheme, a sender belongs to a PKI setting, while a receiver belongs to an IBC setting. PI-HDATK is denoted by this kind of DATK scheme as follows.
4.1 Syntax
A PI-HDATK scheme comprises six algorithms below:
Setup: Given 1k, the PKG obtains the params and a master private key s. Due to params are public, we neglect them in other algorithms.
PKI-KG: A user in the PKI setting calculates a secret/public key pair (sk, pk).
IBC-KE: A user in the IBC setting transmits its identity ID to the PKG who computes its private key SID and securely transmits it to the user. Here, we assume that the user’s public key is its identity ID.
Sym: Given a sender’s secret key sks, public key pks, and a receiver’s identity IDr, the sender produces an encryption key K and state information ω.
Encap: Given a tag τ and the state information ω, the sender creates an encapsulation ϕ.
Decap: Given a sender’s public key pks, a receiver’s identity IDr, private key
If (k, ω) = Sym(sks, pks, IDr) and ϕ = Encap(ω, τ), then
4.2 Security notions
The confidentiality and deniable authentication should be satisfied for the PI-HDATK scheme. For IND-CCA2 security in a PI-HDATK scheme, it is assumed that this game below is between
“IND-CCA2” game (Game-IV):
Setup.
Phase 1.
Key extraction queries: This is identical to Game-I.
Symmetric key generation queries:
Encapsulation queries:
Decapsulation queries:
Challenge.
Phase 2.
Guess.
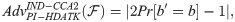
Definition 4. A PI-HDATK scheme is IND-CCA2 secure if a PPT adversary
In the above definition, it is allowed that
For deniable authentication, the security concept, deniable authentication against adaptive chosen message attacks (DA-CMA) is employed in our design.
For DA-CMA security in a PI-HDATK scheme, it is assumed that this game below is played between
“DA-CMA” game(Game-V):
Setup. This is identical to Game-III.
Attack. This is identical to Game-III.
Forgery.
DAD(σ*,
Definition 5. A PI-HDATK scheme is DA-CMA secure if a PPT adversary
In the aforementioned definition,
5 A hybrid PI-HDAE scheme
Fig 2 depicts a hybrid PI-HDAE scheme that constitutes a PI-HDATK and a DEM. In DEM part, the ciphertext is a tag. This construction provides simple description. Theorems 1 and 2 present the security consequences.

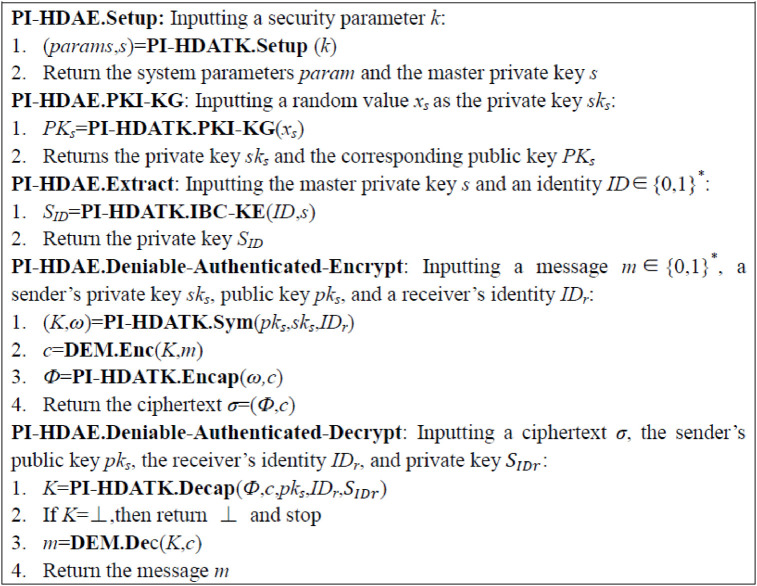
Construction of PI-HDAE from PI-HDATK and DEM.
Theorem 1. Let a hybrid PI-HDAE scheme constitute a PI-HDATK and a DEM which are IND-CCA2 and IND-CPA secure, respectively, PI-HDAE is IND-CCA2 secure. to be specific, we receive
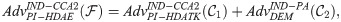
Proof: See Appendix 1.
Theorem 2. Let a PI-HDAE constitutes a PI-HDATK and a DEM. If PI-HDATK is DA-CMA secure, PI-HDAE is also DA-CMA secure. to be specific, we receive
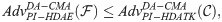
Proof: Refer to Appendix 2.
6 A PI-HDATK scheme
There are six algorithms to describe our proposed scheme. Fig 3 shows the main description. In DEM part, a tag is the ciphertext. This construction provides simple description and realizes better universal security.

The main contribution of PI-HDATK.
6.1 Basic knowledge
In this section, we provide bilinear pairings properties, decisonal bilinear Diffie-Hellman problem (DBDHP), and bilinear Diffie-Hellman problem (BDHP).
Let G1, G2 be an additive group and a multiplicative group, respectively. P is a generator of G1, and G1 as well as G2 have the same prime order q. A bilinear pairing is a map e: G1 × G1 → G2 with the following properties:
Bilinearity: e(aP, bQ) = e(P, Q)ab for all
Non-degeneracy: There exists P, Q ∈ G1 such that e(P, Q) ≠ 1.
Computability: There is an efficient algorithm to compute e(P, Q) for all P, Q ∈ G1
The modified Weil and Tate pairings are the admissible maps ([42–48] offer more information). This scheme’s security depends on the difficulty of dealing with the flllowing problems.
Definition 1. Decisional Bilinear Diffie-Hellman Problem (DBDHP). In the light of bilinear pairings basic definition as above mentioned, DBDHP is to determine θ = e(P, P)abc given (P, aP, bP, cP) with
Definition 2. Bilinear Diffie-Hellman Problem (BDHP). In the light of bilinear pairings basic definition as above mentioned, BDHP is to calculate e(P, P)abc given (P, aP, bP, cP) with
6.2 Our scheme
Setup. Given G1, G2, P, and e as in Subsection A of Section VII. Let k be a security parameter (q ≥ 2k) and n be a a DEM’s key length. H1, H2, H3 are three cryptographic hash functions, where H1: {0, 1}* → G1, H2: {0, 1}* × G1 × G2 → {0, 1}n and
PKI-KG. A user belongs to a PKI setting elecets
IBC-KE. A user belongs to an IBC setting gives its identity ID to the PKG. The PKG calculates its private key SKID = sQID(QID = H1(ID)) and securely transmits it to the user. Here, IDr denotes the receiver, and pkr = IDr
Sym. Given a sender’s private/public key pair (sks, pks), and a receiver’s identity IDr, the algorithm below is done.
Pick
Compute
Calculate K = H2(t, pks, IDr).
Return K and ω = (r, t, sks, pks, IDr).
Encap. Given a tag τ and the state information ω, the algorithm below is done.
Compute h = H3(τ, t, pks, IDr).
Compute S = (hsks + r)Ppub.
Compute
Compute V = hpks.
Compute σ = (W, V).
Decap. Given a tag τ, an encapsulation σ, a sender’s public key pks, a receiver’s private key
Compute
Compute h = H3(τ, t, pks, IDr).
If V = hpks, output K = H2(t, pks, IDr); if not, return the symbol ⊥.
The consistency of the designed HDATK scheme can be verified. Because
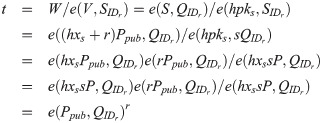
6.3 Security
Theorems 3 and 4 offer the security consequences for PI-HDATK.
Theorem 3. Under DBDH assumption, in ROM,
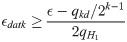
Proof: Refer to Appendix 3.
Theorem 4. Under BDH assumption, in ROM,
Proof: Refer to Appendix 4.
7 Performance
We conduct a main computational cost comparison of the construction with existing schemes LZJ [35] and HDA-I of LHO [39] listed in Table 1. The point multiplication in G1, the exponentiation calculation in G2, the addition calculations in G1, and the pairing calculation in G2 are denoted by PM, EC, AD, and PC, respectively. We ignore XOR, and hash function since they are trivial. In all computational cost, the PC evaluation is the most time-consuming. From Table 1, it shows that the computation overhead of our scheme is less than that of LZJ [35], but more than that of the HDA-I of LHO [39]. It is noted that LZJ [35] is not a heterogeneous DAE scheme which is not catered for the LBS and HDA-I of LHO [39] cannot achieve confidentiality.
An experiment is conducted on the PBC library with A pairing [49]. The A pairing is designed on an elliptic curve y2 = x3 + x mod p for some prime p ≡ 3 mod 4. As needed, we set the order of G1 is q and the library’s embedding degree to 2. Here, 80-bit, 112-bit, and 128-bit denotes three kinds of AES [50] key size security level, respectively. Table 2 shows the description for different security levels.

| Security level | Size of P | Size of q |
|---|---|---|
| 80-bit | 512 | 160 |
| 112-bit | 1024 | 224 |
| 128-bit | 1536 | 256 |
We implement the experiment on an Intel Pentium(R) with 2,048 MB of RAM (2,007.04 MB available) and Dual-Core processor running at 2.69 GHz. On this machine, a PM takes 15.927 ms, and an AD requires 0.065ms employing an ECC with q of 160 bits. A PC and an EC take 26.68 ms and 3.126 ms, respectively. LZJ [35] takes 146.939 ms, HDA-I of LHO [39] takes 101.206 ms, and our scheme takes 130.947 ms. Fig 4 depicts the comparative computational cost for LZJ [35], HDA-I of LHO [39], and our scheme. From Fig 4, we can see that the implementation results are consistent with the theoretical analysis.

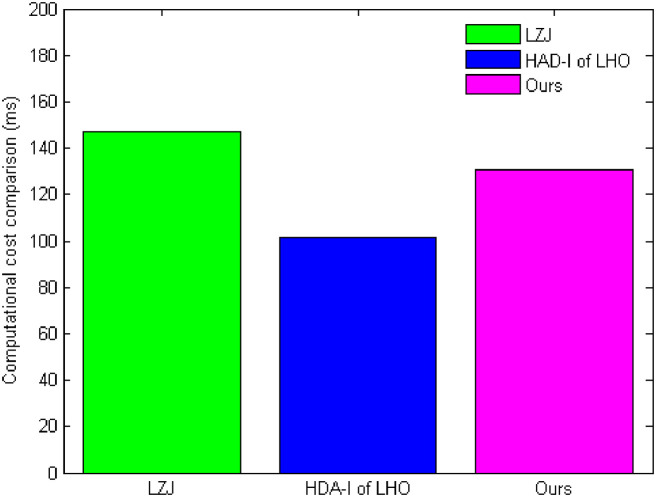
Computational cost comparison.
For the communication cost, LZJ [35], HDA-I of LHO [39], and our scheme are |m| + |G1| + |G2|. They possess the identical communication cost. |x| is the size of x. For 80-bit security level, |p| = 512bits, |G1| = 1024bits, |q| = 160bits. If the standard compression techniques are used, G1 can be reduced to 65bytes. G2 = 1024bits = 128bytes. Therefore, the communication cost of the three schemes is |m| + |G1| + |G2| = | m| + 65 + 128 = |m| + 193bytes. For 112-bit security level, |p| = 1024bits, |G1| = 2048bits, |q| = 224bits. Using the standard compression technique, G1 can be reduced to 129bytes. G2 = 2048bits = 256bytes. Therefore, the communication cost of the three schemes is |m| + |G1| + |G2| = |m| + 129 + 256 = |m| + 385bytes. For 128-bit security level, |p| = 1536bits, |G1| = 3072bits, |q| = 256bits. Using the standard compression technique, G1 can be reduced to 193bytes. G2 = 3072bits = 384bytes. Therefore, the communication cost of the three schemes is |m| + |G1| + |G2| = |m| + 193 + 384 = |m| + 577bytes. Fig 4 shows the communication cost at different security level. It shows that from Fig 5 the 80-bit security level is our best choice for the current computing condition.

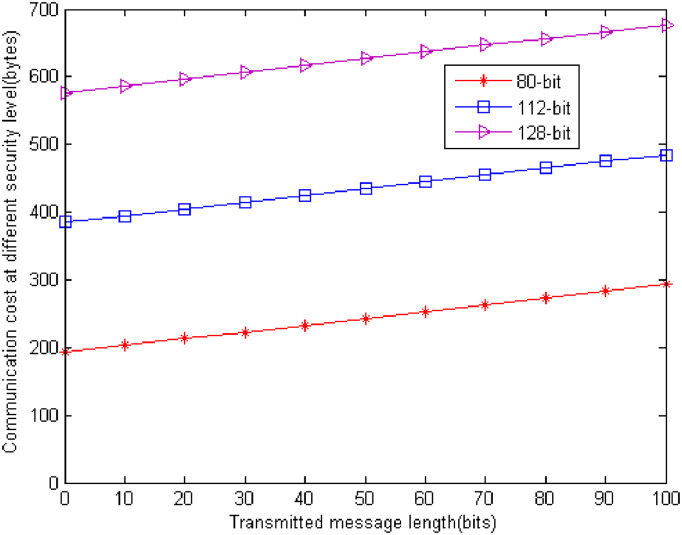
Communication cost at different security level.
8 Application
Zeng et al. [51] presented a deniable ring authentication for protecting the LBS privacy. In their scheme, the user’s identity is anonymous to the LBSP and he/she can deny that he/she sends the requested location information to LBSP. However, the entities are all in the same environment and the requested location information is sent in plaintext. Any adversary can monitor or intercept this sensitive information. Therefore, to better resolve this issue, utilize our designed HDAE scheme in LBS systems to render the transmitted message in ciphertext. The specific communication process is as follows:
A user in a PKI environment wants to request the location-based service m from the service provider (SP) in an identity-based environment. It first executes the PKI-KG algorithm to produce its private/public key pair (sks, pks) and executes DAE(m, sks, pks, IDr) to create a ciphertext σ. The user then passes the resulting σ to the SP. When the SP receive the LBS request, it first requests a private key
9 Conclusion
In this paper, we designed a hybrid DAE scheme which comprises a PI-HDAE scheme and a DEM scheme. The entities are in a heterogeneous system where the sender belongs to the PKI environment, while the receiver belongs to the IBC environment. Our construction can achieve confidentiality and deniable authentication in a single logic step. We give a formal security proof in the ROM. Our performance results show that this construction is secure and efficient. Furthermore, we present an example and apply our design to LBS system for better service.
Appendix 1
Proof: Our proof strategy is shown below. The modified games Game0, Game1, Game2 are defined in [52, 53]. The games’ difference lies in how the environment replies
The lemma from [54] is employed as follows.
Lemma 1. Let E, E′, and F be events defined on a probability space such that Pr[E∧¬F] = Pr[E′∧¬F]. Then, we get |Pr[E] − Pr[E′]| ≤ Pr[F].
Game0: We execute key extraction algorithm to simulate adversary’s view in a real attack. Then we utilize the produced key to reply
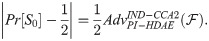
Game1: In this game, we only alter how the DAD oracle replies
This change does not affect
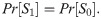
Lemma 2. The running time of a ppt algorithm
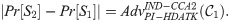
Proof: The proof below gives how to design
The game is between
Setup:
Phase 1: Issue a symmetric key generation (SKG) query on IDj to gain K. Calculate c = DEM.Enc(K, m). Issue a key encapsulation (KES) query on c to gain ϕ. Return σ = (ϕ, c).
When
Issue a KD query on (ϕ, c, IDj) to get K.
If K = ⊥, abort.
Calculate m = DEM.Dec(K, c) and output m.
Challenge: Pass IDj to its challenger to gain Kβ for β ∈ {0, 1}. Elect δ ∈ {0, 1}. Compute c* = DEM.Enc(Kδ, mδ). Pass c* to its challenger to gain ϕ*. Return σ* = (ϕ*, c*) to
Phase 2:
Guess:
When Kb is a genuine key,
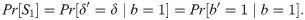
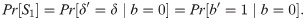
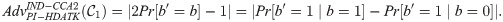
Lemma 3. The running time of a ppt algorithm
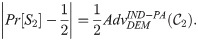
Proof: The proof below gives how to design
Pr[S2] is the probability that
Appendix 2
Proof:
Setup:
Attack: When
Fogery:
Visibly, this is a perfect proof. If
Appendix 3
Proof:
Before
A KES query’s encapsulation ciphertext will not be employed in a KD query.
Setup:
Phase 1: H1
queries: H2, H3
queries: When Key extraction queries: When Generation symmetric key queries: Key encapsulation queries: Key decapsulation queries:
Challenge:
Phase 2:
Guess:
Now we calculate
E1
E2
E3
We show that Pr[¬E1] = 1/
Because
p1 = Pr[β′ = β∣(Kβ, ω*) = Sym(pks, sks, IDr)] and
and
We get
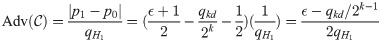
O(qgsk + qke + qkd) is
Appendix 4
Proof: we have to let our design fit into the signature scheme described in [54], where the simulation step can be simulated in the absence of the sender’s private key (i.e., absence of the master private key). On this occasion, we need an approach to resolve the BDH problem.
First, we observe that the PI-HDATK scheme accords with the requested three-phase honest-verifier zero-knowledge identification protocol, where σ1 = t is the commitment, h = H3(τ, t, pks, IDr) is the hash value, and σ2 = W is the answer.
Second, a simulation step is shown and an approach of how to resolve the BDH problem is given. Given (P, aP, bP, cP) of BDH problem,
Setup:
Attack: H1
queries
H2, H3 queries, KE queries, GSK queries, KES queries, and KD queries are identical to them in Theorem 3.
Fogery:
From the forking lemma [54] and the lemma on relationship between given-identity and chosen-identity attack [55], if
Acknowledgements
The authors thank the anonymous reviewers and the Editor for the constructive comments and generous feedback.
References
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
 Heterogeneous deniable authenticated encryption for location-based services
Heterogeneous deniable authenticated encryption for location-based services
